OLLI Course: P@s$w0rdz
OLLI Course: P@s$w0rdz
Course Description | Instructor | References

are now spent entering passwords into my phone and computer."
by eric.delcroix is licensed under CC BY-NC-SA 2.0
Course Description
- next: ?
- previous: Ashland: Fall 2023; Zoom: Fall 2021; Fall 2020 (twice); May 2020, Apr 2020; Ashland: Fall 2019
- Course URL:
https://communicrossings.com/passwords
or: https://communicrossings.com/olli-course-psw0rdz
this site will continue to be available and updated - Course Handouts: web pages as .pdf (offline copy, with active links)
available before / during / after the course -- updated occasionally: - P@s$w0rdz .pdf; 4.5Mb; 147 pp (landscape); [updated: 9/18/2023]
- Passwords: References .pdf; 0.5Mb; 52 pp; [updated: 9/18/2023];
article links from OLLI Course: Be Safer on the Internet: Browsing: Passwords - Recent headlines suggest that "passkeys" -- which use biometrics
or other devices for authentication -- could completely replace passwords.
Understand passkeys' current limitations. -
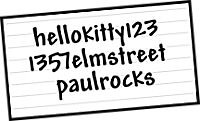
"Passwords" by paul.orear
is licensed under CC BY-SA 2.0In the meanwhile, learn how to create strong passwords for your devices and accounts.
Reduce stress and declutter your brain by remembering just one strong primary password;
a "password manager" app can store, encrypt and fill-in your online logins and other information;
in particular, I will discuss 1Password* and contrast it with other password managers
and storage methods (such as paper, encrypted spreadsheet, etc.). - Amp up security for sensitive accounts: provide unique secret answers,
add recovery information, and enable Multi-Factor Authentication (MFA) via app or phone. -

"when someone's password""
by Dianna Geers
is marked with CC0 1.0.
"When someone's password is PASSWORD"Discover if an account has been hacked, and when to change its password.
Other privacy and security topics and advice will be included as time permits. - *I will demonstrate 1Password for Mac and iPad.
The menus and commands for 1Password on different platforms
(Android, ChromeOS, iOS, Linux, Mac, Windows) and browsers
should be almost identical in user interface and functionality. - For other password managers, the concepts and features should be very similar,
though analogous commands and menus may be named and organized differently. - "Getting information off the Internet is like taking a drink from a fire hydrant."
~Mitchell Kapor -

"passwords" by Dianna Geers
is licensed under CC0 1.0The same might be said about this course
-- many topics; much detail; too little time; it can seem overwhelming. - It's a much shorter (3-session) version of earlier Be Safer on the Internet,
but focused only on passwords -- comparison of topics for all Internet Privacy & Security courses - I'll highlight and introduce the most important issues.
- You can even take the course again,
if there's something you missed, or to hear the latest advice.
 About the Instructor
About the Instructor
| Non-expert Online Practices 1. Use Antivirus Software 2. Use Strong Passwords 3. Change Passwords Frequently 4. Only Visit Websites They Know 5. Don't Share Personal Info |
Expert Online Practices 1. Install Software Updates 2. Use Unique Passwords 3. Use Multi-Factor Authentication 4. Use Strong Passwords 5. Use a Password Manager |
References
- 5 easy tasks that supercharge your security:
1. Use a password manager;
2. Enable two-factor authentication;
3. Stay safe with security software;
4. Don’t use a (Windows) admin account;
5. Back up your data; PC; 5/22/2023 - 6 Things You Need to Do to Prevent Getting Hacked:
1. Use Multi-Factor Authentication;
2. Get a Password Manager;
3. Learn How to Spot a Phishing Attack;
4. Update Everything;
5. Encrypt Everything;
6. Wipe Your Digital Footprint; Wired; 8/29/2021 - Five Tech Commandments to a Safer Digital Life:
1. Thou Shalt Not Use Weak Passwords
2. Use Multifactor Authentication
3. Thou Shalt Not Overshare
4. Thou Shalt Not Share Data About Friends
5. Remember to Stay Skeptical; NYT; 3/24/2021 - Why You Need a Password Manager. Yes, You.:
"It's the most important thing you can do -- alongside keeping your operating system
and Web browser up-to-date, and enabling two-factor authentication
-- to keep your data safe"; NYT; 9/2/2019 - References: Be Safer on the Internet: Passwords: web

 E-books recommended -- but not required:
E-books recommended -- but not required:- Take Control of Your Passwords, sample, cheat sheet [v 3.2; 7/28/2021]
- Take Control of 1Password, sample [v 6.0.1; 3/3/2023]
- If I don't offer student-discounted copies of these ebooks,
you can save 30% if you buy 3 Take Control ebooks,
or are a Tidbits member (membership discount on 1Password) - Steve's crosswords: Not Stroganoff. Try Again; Open Sesame
P@s$w0rdz: Passkeys -- No More Passwords?
P@s$w0rdz: Passkeys -- No More Passwords?
Intro | Passkeys | Biometrics | Other Options
Introduction
- You may think that there's no need for this course
after seeing headlines like the following: - Passkeys may not be for you, but they are safe and easy -- here's why
answering common questions about how passkeys work; Ars; 5/12/2023 - Embrace the Passwordless Future of Passkeys LH; 5/9/2023
- Everything to Know About Passkeys for a Password-Free Future NYT; 1/11/2023
- Why Passkeys Will Be Simpler and More Secure Than Passwords TB; 6/27/2022
- A Big Bet to Kill the Password for Good Wired; 3/17/2022

is licensed under CC0 1.0
Passkeys
- Passkeys (aka 'multi-device FIDO credentials') authenticate you safely with a web service
- using biometrics: fingerprint and iris scanners, voice and facial recognition
- or other devices: phone, laptop, USB security tokens, smart cards
- FIDO2 is a very secure standard, and interoperable across devices;
it combines -- warning: geek speak!: - FIDO ("Fast IDentity Online") Alliance's Client to Authenticator Protocol 2 (CTAP2)
- World Wide Web Consortium (W3C)'s Web Authentication (WebAuthn) standard
- Benefits:
- convenient: use biometric or device authentication with sites instead of a password
- secure: client doesn't send password and sites don't store passwords -- no password-database breaches
- standard: tech giants, e.g., Apple, Google, and Microsoft, are starting to introduce passkey support;
e.g., Apple supports passkeys in iOS/iPadOS 16+, macOS 13+ (Ventura, Sonoma), watchOS 9+ - interoperable: passkeys are synced to whatever cloud storage method your device uses,
such as iCloud Keychain on Mac and iPhone or Google Password Manager on Android and ChromeOS - Drawbacks (current):
- device PIN: your passkeys could be accessed if someone has/guesses your device's weak PIN/password
- site support: limited number of web sites: passkeys.directory
- mixed platforms/ecosystems: e.g., Apple, Microsoft and Google
transferring credentials between different device families may not work smoothly (or at all) - older devices/OSes: you'll still need passwords if passkeys are unsupported
- missing/lost device, unrecognized biometric, share with a friend: you'll still need a password
- biometric spoofing: e.g., Attackers can bypass fingerprint authentication with an ~80% success rate
via fake fingerprints, if enough login attempts allowed (only high-profile targets need worry?) - government intrusion: you can be compelled to provide something you have: biometrics, device.
You currently can refuse to reveal something you know: PIN, password;
US courts have interpreted the Constitution's 5th Amendment (self-incrimination) differently;
Electronic Frontier Foundation (EFF) recommends using a PIN instead of biometric unlocks
for your device if you’re concerned about potential legal (or illegal) access by law enforcement.
is licensed under CC BY-NC-SA 2.0
Biometrics
- Even without passkeys, you can already use a fingerprint or face scan as a convenient shortcut,
or to augment Multi-Factor Authentication (which we'll cover at the end) - For now, you still need a strong passcode
for initial setup, after updates / restarts, and as a fallback. - Require passcode: periodically (set timeout preference), or immediately (after power off).
- iOS:
Settings > Passcode > Require Passcode: Immediately,
or After ___ minutes/hours - When travelling (esp. internationally) or leaving device unattended, unlike macOS,
there's no iOS 'Lock Screen' command to force a passcode prompt upon next wakeup. - Besides actually powering down the iPhone/iPad, another way to require a passcode:
~4 unrecognized fingerprint attempts, using a finger different from the ones used to train Touch ID. - Fingerprint sensor, e.g., Apple Touch ID: Accuracy? Strength? Injured digit? Gloves?
- If compromised, you can't change. Spoofed?
- video: Use Touch ID to unlock 1Password on your iPhone or iPad
- Facial recognition, e.g., Apple Hardware Security & Biometrics: Face ID: Accuracy? Strength? Face mask?
If compromised, you can't change. Spoofed? - Is vendor storing your biometric data, and how securely?
- Allow 1Password (or other password manager) to open your password vault with biometrics?
is it as strong as your primary password (and your device password) -- security vs. convenience tradeoff - Safer Internet: Browsing: Protect Passwords: Biometrics, Fingerprints, Facial Recognition; Passkeys
Other Options
- When applicable/available, passkeys are a huge security improvement over many users' poor password practices
- Some related current approaches are discussed under Storage: Apple Keychain, Single Sign-on
- However, a good password manager (PM) can provide these and other benefits today
while providing a transition to tomorrow: - central password: password for encrypted vault stronger than any device PIN/password
- secure, universal: works on all sites
- passkeys: included in newer PMs, e.g., 1Password
- interoperable: works across different platforms and on older OSes
- other info: store and fill-in, e.g., credit cards, personal info, etc.
- 1Password is finally rolling out passkey management
save passkeys and synchronize them across devices and platforms; Verge; 5/16/2023 - The Best Password Managers to Secure Your Digital Life some discussion of passkeys; Wired; 3/27/23
- We'll cover password managers more in upcoming sections.
P@s$w0rdz: Weak Passwords
P@s$w0rdz: Weak Passwords
Quotes | Weak vs. Strong | References

is licensed under CC BY 2.0
Quotes
- "I speak the pass-word primeval" ~Walt Whitman, Song of Myself
- "Don't use 'beef stew' as a computer password...
- The 25 Most Popular Passwords of 2018 Will Make You Feel Like...
- "Changed my password to fortnight but...
-

"the password is courage"
by russelldavies is licensed under CC BY-NC 2.0 - What do passwords and teenagers have in common?...
- My email password has been hacked again...
- "'123456' is a weak one...
- "49-Across: It may require letters, a number and a special character...
- "They'll Never Guess," The Week, 3/18/2022; crossword, solution;
16-A. Keyboard sequence that's the 18th most common computer password,...
19-A. The 4th most common password...
39-A. 13th most common password,...
56-A. 19th most common password,...
61-A. Most common single-character password,...
9-D & 24-D. Numerals that are the 16th most common password --...

Scegli sempre delle password molto forti.
“1234” non è una password forte.
No, neanche “password” è una password forte.
Una password forte deve contenere dei numeri
e delle lettere maiuscole; se proprio vuoi fare il..."
by Enza La Frazia is licensed under CC BY-ND 2.0.
translation: "TIP of the week:
Always choose very strong passwords.
'1234' is not a strong password.
No, 'password' is not a strong password either.
A strong password must contain numbers and capital letters;
if you really want to be cool also some symbols like @ & and the like.
No passwords with your name or nick name.
Better to avoid the name of the child, wife or dog,
date of birth and telephone number.
Do not divulge your password, do not tell anyone,
do not enter it on any suspicious link that you received via email.
Ah, one last thing: don't use the same password
for more than one site or service."
What Makes a Password Weak (or Strong)?
- Short vs. long
- Simple vs. complex (larger set of characters available&used)
- Predictable/common vs. random/unusual
- Public vs. private
- Reused vs. unique
- ...
References
- Check if an account was involved in a breach/leak
haveibeenpwned.com: enter email or phone;
"credential stuffing": hackers reuse info from breached accounts
to try logging into other accounts with same username and password - Wikipedia: Lists of the most common 20-25 passwords,
10,000 passwords SplashData annual comparisons, plus other sources - "Worst 25+": 2022; 2021; 2020; 2019; 2018;
2017; 2016; 2015; 2014; 2013; 2012; 2011; 2010 - Top 200 most common passwords compare by country; Nordpass
- 100 latest world's worst passwords — don't use any of them Tom's Guide; 7/6/2020
- 100,000 Leaked Passwords UK National Cyber Security Centre;
.txt; from haveibeenpwned.com  Ten Years Of Breaches In One Image
Ten Years Of Breaches In One Image
Nearly 8 billion usernames have leaked since June 2011; Verge; 6/8/2021- National Password Day project:
A unique password for every website you go to
(typical advice): strong, unique passwords that you can remember,
and/or subscribing to a password manager;
additional authentication factor; USA Today; 5/7/2020 - Why 'ji32k7au4a83' Is a Remarkably Common Password
Taiwanese keyboard transliteration translates to 'my password'; Giz; 3/4/2019 - Kanye West Has Literally the Worst iPhone Passcode
You Could Ever Have000000; MB; 10/11/2018 - Snowden's 'Sexy Margaret Thatcher' Password Isn't So Secure
MargaretThatcheris110%SEXY; Wired; 4/2015 - Crossword (by Steve; on right): Not Stroganoff. Try Again
- Refs: Password Strength
P@s$w0rdz: Stronger Passwords
P@s$w0rdz: Stronger Passwords
Quotes | Why? | How? | Hackers; Credential Stuffing |
Types: Memorable or Complex |
Remember? | Before Jumping In

is licensed under CC BY-NC-ND 2.0
Quotes
- During a recent password audit, an OLLI student
was found using the following password:
"MickeyMinniePlutoHueyLouieDeweyDonaldGoofySacramento"
When asked why such a long password, the student replied... - "Passwords are like underwear:...
- "This is my password," said the King as he drew his sword...
- Passwords for really forgetful people:...
- Login incorrect....
- "I was going to change my password to be one of my favourite places in France...
- Rick Astley's guide to password management...
- A teenager at a funeral asks the priest for...
- Set your wifi password to 2444666668888888...
- A man needs WiFi at the local pub and asks for the password.
The bartender replies: You need to buy a drink first...
- An IT guy goes to the dentist.
Dentist: Have you been flossing regularly?...
 USER: I can't get on the Internet.
USER: I can't get on the Internet.
SUPPORT: Are you sure you used the right password?...
- Normal people use their...
- "49 Across: It may require letters, a number and a special character...
- Clean water is like your password...
- "I got asked to leave karaoke night for singing 'Danger Zone' 7 times in a row...

is licensed under CC BY-NC-SA 2.0
Why (Strong) Passwords?
- "Passwords are one of the primary pain points
in our modern digital existence."
~Why You Need a Password Manager - Until a more effective, secure and reliable
form of authentication appears,
passwords are a necessary evil -- for now. - Strong passwords can prevent access
to our financial and personal information
by criminals and unethical governments. - Even if you think a site is unimportant,
it may store some personal info
with more added in the future. - If you reuse the same password on other sites
and one of them is hacked, the attacker could
log in as you on all your 'throwaway' sites
and piece together your data fragments
for a more complete dossier about you. -

Authorization by XKCD is licensed under a
Creative Commons Attribution-NonCommercial 2.5Passkeys (discussed earlier) might eventually replace the need for many passwords.
However, they may work best currently for recent devices from one vendor
-- perhaps only with the latest (upgraded) OS versions,
and only for some browsers and accounts/sites. - You still need strong device passwords for computer, tablet and/or phone
-- passkeys are only as secure as the weakest device PIN/password. - You need to lock/logout device when away,
to avoid access to your account, already logged-in sites, password resets, etc.
[on right: general problem for all OSes & devices]
What Makes a Password Stronger?
-

"How to choose a password" by thewikiman
is licensed under CC BY 2.0"To put it simply, a good password is one that you won't forget
[or can copy] but that no one else (human/computer) can guess."
~Joe Kissell, Take Control of Your Passwords - Unique: don't use the same password on multiple sites
-- or a password anyone else has used! - Hackers add passwords from compromised sites to their
lists of leaked credentials then use credential stuffing (below),
hoping that someone reused that password for other sites - Check if a site has been breached for your username(s):
1Password:Watchtower, haveibeenpwned.com
-- update that account, and any accounts with the same password - Linkedin Scraped Data Breach example:
email from haveibeenpwned; 10/2/2021,
update from LinkedIn; 6/29/2021 - Don't log into 3rd party sites with your Facebook
or Google credentials ("Single Sign On") -- more later. - Uncommon: avoid 'obvious' ones and public info,
e.g., names of pets, sports teams, single dictionary word,
keyboard pattern, popular quotes, worst 25 of 2017, etc. - Unpredictable: don't "strengthen" a weak password like everyone else, e.g.,
"Numbers? You'll likely add a "1" at the end.
Capital letters? You'll capitalize the first letter.
Special characters? Frequently exclamation marks."
~Rules for strong passwords don't work, researchers find CNet; 11/12/2020 - The Password Game will make you want to break your keyboard in the best way
Game; Ars; 6/28/2023 - A compilation of sites with dumb password rules
-
"Yummy Student Password Matrix"
by The Daring Librarian
is licensed under CC BY-NC-SA 2.0Avoid predictable patterns, i.e., a 'base password' combined with a sitename (or its abbrev.),
e.g., "olli-facebook123"?
Could a hacker having that password and inferring a pattern,
guess similar passwords, e.g., "olli-amazon123", "olli-gmail123"? - Password Bingo uses same key/pattern on different bingo cards
to generate/lookup a password -- cute, but insecure if hint includes card# - Unchanging: despite obsolete advice, passwords don't usually need to be changed
unless they're weak, reused or compromised -- though some sites will still insist. - Never Change Your Password
1. If it's sufficiently strong; 2. If you created a unique one for each account;
3. Unless there's a security breach where it's stored; TB; 3/5/2022 - Long: the longer, the stronger: 24-100 characters
- Attackers don't bother brute-forcing long passwords, Microsoft engineer says
77% of attempts used a password between 1 and 7 characters. over 10 characters in only 6% of cases;
only 7% included a special character; 39% actually had at least one number;
none included white space; 11/22/2021 -

Account Problems by XKCD is licensed
via Creative Commons Attribution-NonCommercial 2.5Complex: add (unusual) punctuation, in addition to upper/lowercase, digits
-- if valid for site and typable on your device's keyboard. - Hackers know about appending the same symbol many times,
e.g., ".....$$$$$$$$$", known as "haystack" technique
-- the length increase provides illusionary strength. - Hackers substitute similar-looking numbers or characters,
known as leet (or “1337”) technique
-- so, "P@s$w0rdz" (course title) is no stronger than "Passwords",
nor is "p455\/\/0rd", etc. [below right: $nakesOnAPlane isn't strong] -

""Secure password of the week"
by Simon Lieschke is licensed under CC BY-NC 2.0Complexity is great, but may be more difficult to type
-- longer is more important if you can't autofill or paste or have to remember it. - Unknown: a strong password is worthless if revealed / shared.
- Olympics Broadcaster Announces His Computer Password on Live TV video; 7/26/2021
- The Advanced Spellchecker in Chrome and Edge Saves Everything You Type
-- Even Passwords LH; 9/20/2022 - Or revealed via insecure software or careless user or company practices (details: Be Safer on the Internet);
see also: Steps to Simple Online Security good overall summary 4/1-4/15/2022 -

from: takecontrolbooks.com
Take Control of Your Online PrivacySummary below:
- Install latest software&security updates for operating system,
applications and browser extensions. - Set strong memorable password / PIN for device user account to protect files,
information, contacts, etc.; extra credit: encrypt storage and backups - Use password manager to navigate to the correct site.
- Enter passwords only on official, secure (https) pages.
SSL/TLS (Secure Sockets Layer/Transport Layer Security) encrypts web and email - Don't click on links in phishing emails;
hovering over a link may not popup true destination;
avoid shortened URLs to access login / form pages;
don't log into fake sites aka "social engineering" - 2023 cyber-attacks targeted a vulnerability in the MOVEit filesharing technology
used by many federal & state agencies and corporations around the world.
This breach exposed personal information of millions of people,
including social security numbers in many cases. - Take advantage of any credit monitoring service that your bank or financial institution offers;
set up proactive credit freezes (prevents others from opening a credit card or taking out a loan with your SSN)
and/or deal with identify theft -- see Safer Internet: Identify Theft, Credit Freeze - You can "thaw" all of the credit freezes temporarily later if you do want to apply for credit.
- Don't share passwords (or other sensitive info) via email
- If you must share, consider more secure transfer methods, e.g.,
- How to share a password via AirDrop
from KeyChain, even if iCloud syncing off; MW; 10/23/2020 - 1Password 7.9 Adds Secure Password Sharing;
blog.1password.com; one-use or expiring link,
optional email verification; TB; 10/19/2021 -
"That awkward moment when someone's staring at
your keyboard while you're typing your password."
by QuotesEverlasting is licensed under CC BY 2.0Limit any password sharing to less important accounts,
e.g., streaming services may allow sharing without revealing actual password,
or use MFA (Multi-Factor Authentication) to protect account-level changes - Don't enter password / PIN while anyone is looking at your screen over your shoulder,
or when using others' or public devices since those might contain malware, i.e., keyloggers - Prevent / remove malware on devices you use.
- Connect to Wi-Fi via strong typable password -- encrypted WPA2 (or WPA3).
Otherwise, hackers can "sniff" for username/password combinations
as they’re sent from unencrypted (http:) pages on your computer to a server;
if strong W-Fi encryption not available, use a VPN?;
also set strong admin password for your router. - Reinforced: passwords-alone are often not secure enough; later sections:
-
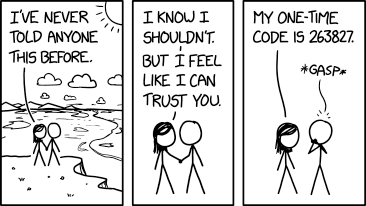
Never Told Anyone by XKCD is licensed
via Creative Commons Attribution-NonCommercial 2.5 - Usernames
- Multi-Factor Authentication (MFA) temp codes via SMS text message or authenticator app.
Have browser prompt for MFA code each time
-- saved authentication cookies can be stolen from browser or intercepted in transit.
Don't provide your MFA codes via phone/text to fake customer support.

is licensed under CC BY-NC 2.0
How Hackers Find Passwords
-- or Credential Stuffing Explained
- Don't use the word "EGG" for your password...
- In an attempt to deter computer hackers I've changed all my passwords to 'Brazil Nut'...
- A (seemingly) alarming news article
-- especially since many of us have used Zoom: - Credentials for 500,000+ Zoom accounts are being sold
on the dark web and hacker forums
Threat actors attempt to login to Zoom using account credentials
[usernames, passwords] leaked in older data breaches. The successful logins
are then compiled into lists that are sold to other hackers; BC; 4/13/2020 -
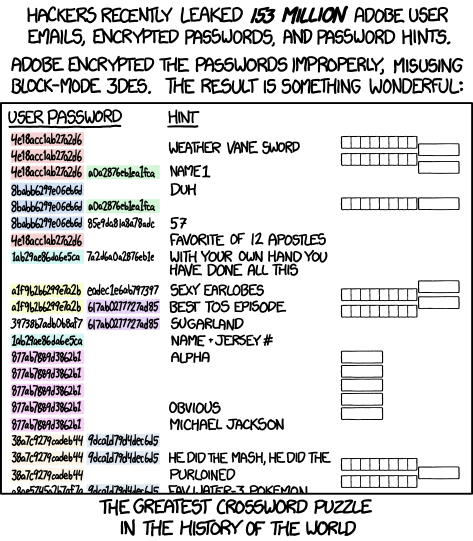
Encryptic by XKCD is licensed under a
Creative Commons Attribution-NonCommercial 2.5 LicenseShould you be worried? change password? uninstall Zoom?
switch to another product (with same or different privacy & security issues)? - Summary: Zoom wasn't hacked.
If a user had created a new Zoom account
with a password reused from a different site (now breached)
or phished from a fake Zoom email & site,
a hacker can easily login into that account
-- unless user had quickly changed the password, or enabled MFA - Curious about why this isn't a Zoom-specific issue,
and the roles of companies, users, hackers -- read on.
Companies
- Some companies have sloppy server & IT practices:
old insecure web/database software, poorly paid/trained staff,
weak/no password protection for sensitive files, etc.
-- attacks on their sites can lead to data breaches
(see Hackers below) -

"Top 500 Passwords" by mkandlez
is licensed under CC BY-NC 2.0Most companies provide client (user) software
with security bugs, or missing or misconfigured
privacy or security features / settings
-- when these problems are discovered,
some companies may be slow to offer software fixes,
or deny/ignore/downplay the problem. - Although many client issues emerged with early users,
Zoom promptly and frequently issued software client updates;
there have been no apparent server problems
-- so, what's the cause of the credentials scare (above)?
Users
- Many users create accounts with the same userid/username,
either because it's simpler to remember,
or sites require using an email address
-- and many users may have only one email. -
"password problems" by Dianna Geers
is licensed under CC0 1.0Some reuse the same password from an existing account
when creating a new account. - Some users, upon receiving an authentic-looking,
alarming (phishing) email about a problem with account access,
click on a conveniently provided link,
and submit their username and password
on an authentic-looking site -- directly to a hacker. - Enlightened attendees of my P@s$w0rdz or
Be Safer on the Internet courses hopefully use unique passwords,
don't click on email links, avoid fake sites,
monitor data breaches, and follow other privacy/security practices.

by GrahamKing is licensed under CC BY-NC-SA 2.0
Hackers
- Hackers don't usually try to log into accounts directly
by guessing passwords -- aka 'brute force', since it's too much work,
and most sites limit login attempts, though they might avoid such limits
by using botnets to attack from different IP addresses. - Hackers use phishing emails/sites to trick
careless users into providing credentials. - Hackers collect/share/sell lists of 'credentials'
-- usernames, passwords, credit cards and/or other info
-- from phishing attacks (careless users), and attacks/leaks/breaches
on various web sites/databases (sloppy company server security) -
"Hashing Password Bad" by Pluke, CC0, via Wikimedia Commons Usernames typically appear in plain text;
credential lists may or may not involve passwords:
most sites encode passwords as "hashes" (numerical codes);
amazingly, a few sites store passwords unencrypted as plain text! - Some of the known breaches in recent years:
Adobe, Anthem, Ashley Madison, Capital One, Charter,
Delta, Doordash, Elsevier, Equifax, Expedia/Orbitz,
Facebook, Hyatt, Kickstarter, Macys, Marriott/Starwood,
Panera, Sears, Slack, Sprint, T-Mobile, Under Armour,
Verizon, Whirlpool, Whole Foods, Zynga, ...
-- but notably not Zoom -
"Hashing Password Hashed" by Pluke, CC0, via Wikimedia Commons Credential stuffing: hackers run searches of known passwords (hashes) against the leaked credentials lists
- If one matches, hacker 'stuffs' those credentials into a different site.
- Hacker often succeeds in logging in
-- unless user had changed password or enabled other measures
Summary
- So, if a user had created a Zoom (or any new) account with a password phished from fake site
or reused from a different breached site, a hacker can easily login into Zoom
-- unless user had quickly changed password, or enabled MFA (paid account only?),
e.g.,Zoom > Admin > Advanced > Security > Sign in with Two-Factor Authentication -

Security by XKCD is licensed via
Creative Commons Attribution-NonCommercial 2.5Unfortunately, password reuse and clicking on phishing links are common
-- potential problems for any site, not just Zoom - So, who enabled the hackers?
The cause in this case (perhaps too bluntly),
PICNIC: "Problem In Chair, Not In Computer",
or PEBKAC: "Problem Exists Between Keyboard And Chair" - Strong password recommendations and other privacy/security advice are summarized above.
is licensed under CC BY-NC-SA 2.0
Two Types of Strong Passwords:
Memorable or Complex
- Memorable: for Devices & Password Manager (PM)
-- 2+ stored in your brain; entered manually (typable) - For phone, 8-10 digit passcode (default is often only 4-6 digits),
or alphanumeric. - For other tablets, computers & password managers,
memorable long (5+ word) phrase;
optional: numbers, capitals, punctuation, misspellings, etc. - Complex: for most Online Accounts
(and private key for FileVault or PM)
-- randomly generated by, stored in, filled-in by PM - If you don't have to remember or type it, why not make it as long and complex as site allows
(24-100 random characters) -- even for 'unimportant' sites? e.g.,
5iFt*b>Qyk[xpjrz@QoC2exanclhLvQ10izlX8hwxK6i=vwix14dwWVznQkvHrWh. - Autofill vs. Manual Entry: a PM may not be able to autofill passwords for certain sites/apps/services
- If you can manually copy/paste the password from PM
or duplicate it so that OS can autofill, e.g., Apple's Keychain,
a Complex password is great. - However, if a site disables paste, or a device has a primitive keyboard interface,
it's easier to enter a Memorable passphrase (minor punctuation, Shifting), e.g., Netflix login on a smart TV.
It may be possible to use another keyboard with the device, e.g., iOS Apple TV Remote app. - So, generally you'll need to remember just 2+ strong passwords,
and the password manager will store all others, which later it'll autofill or you'll paste or type.  In the next section, we'll look at how
In the next section, we'll look at how
to generate different kinds of passwords -- all unique, long and random:- Memorable and/or Typable by you: passcodes (PINs) and passphrases
-- for devices, password manager, sites - Complex [Pastable by PM] character sequences -- for everything else
- Refs: Password Strength; Credential Stuffing

is licensed under CC BY-NC-ND 2.0
How to Remember these Strong Passwords?
- "The only people who like change...
- For those who might forget or lose things -- or prefer to reduce brain clutter,
I strongly recommend using a "password manager" (PM) app. - We'll look at generating, testing and storing passwords;
setting device passwords; and using a PM in upcoming sections;
several PMs mentioned: 1Password, Bitwarden, Dashlane
-- with a focus on 1Password. - We'll discuss tradeoffs of other storage methods:
memory, paper, encrypted spreadsheet, your browser, etc. - 1PW video: No More Sticky Notes
- NYT article: Why You Need a Password Manager. Yes, You. (intro below)
A password manager is a secure, automated, all-digital replacement for the little notepad
that you might have all of your passwords scribbled down in now, but it’s also more than that.
Password managers generate strong new passwords when you create accounts or change a password,
and they store all of your passwords — and, in many cases, your credit card numbers, addresses,
bank accounts, and other information — in one place, protecting them with a single strong primary password.
If you remember your primary password, your password manager will remember everything else,
filling in your username and password for you whenever you log in to a site or app on your phone or computer.
It can proactively alert you when you’re reusing a password or when your passwords are
weak and easy to guess or hack, and some password managers will even let you know when
online accounts are hacked and your passwords have been exposed. For accounts that you need
to share with family members, friends, or co-workers — a joint bank account or mortgage site,
a shared Twitter account, or your insurance and medical records, for instance
— many password managers offer family plans that make it simple to share strong, complex
passwords without requiring multiple people to remember them or write them down.
Learning to use a password manager seems intimidating, but once you start using one
to make strong random passwords that you’re not on the hook to remember, you’ll wonder
how you lived without one. Usually, improving your digital security means making your devices
more annoying to use; a password manager is a rare opportunity to make yourself
more secure and less annoyed.
Before Jumping In...
- Maybe a password manager sounds great already and you're ready to jump in.
- If you're not tech savvy, wait until we introduce password managers in more detail in session 2.
- Otherwise, scan the rest of the course materials yourself,
paying special attention to a few items to avoid common problems. - Password Managers, esp. Getting Started
- Updating Passwords, esp. Strategy
- Recovery & User Names, esp. Recovery
- Wait to enable Multi-factor Authentication on your accounts -- to be covered in session 3.
P@s$w0rdz: Generating Passwords
P@s$w0rdz: Generating Passwords
Quotes | Memorable or Typable: Passcode: Generate; Change | Passphrase: Generate; Change |
Complex and Pastable Character Sequences |
Other Generation Methods

by Dianna Geers
is marked with CC0 1.0
Quotes
- How do you come up with a secure password to protect yourself against hackers?...
- Enter password: 'snowflake'...
- I had to reset my password, chicken,...
Memorable or Typable Passcodes & Passphrases
Generate Memorable Passcode (PIN) for Phone, Tablet
- Phone: 8+ digits; avoid obvious sequences/patterns; e.g., Kanye West: '000000';
The Police Can Probably Break Into Your Phone: phone-hacking tools typically
exploit security flaws to remove a phone's limit on passcode attempts and then
enter passcodes until the phone unlocks. Because of all the possible combinations,
a six-digit iPhone passcode takes on average about 11 hours to guess,
while a 10-digit code takes 12.5 years; NYT; 10/21/2020 - Tablet -- or phone with larger screen/keypad: 5+word passphrase (see below),
or 24+ alphanumeric with punctuation - watchOS: up to 10 digits
- Fingerprint or facial recognition is convenient,
and may be an acceptable risk (see Passkeys:Biometrics), if you:  have a strong PIN/passcode
have a strong PIN/passcode- have an appropriate timeout requiring periodic PIN/password re-entry
- limit login attempts or enable auto-erase
- For a high-profile target, a resourceful criminal might use a fake fingerprint,
contact lens or disguise -- or cut off a body part -- to trick the scanner.
 Generate PIN: PM
Generate PIN: PM
- Note: Password Manager (PM) generator interface may vary
depending on version of 1PW and OS,
e.g., previously, Mac app and browser extension were different. - I created a dummy "TEST PASSWORD" 1PW entry
so that I could easily generate & copy passwords. - 1Password : PIN / PIN Code: # of digits [above: iPad; on right: Mac]
 Generate PIN: OS
Generate PIN: OS
- macOS:
System Preferences > Users & Groups >[on right: Mac]
Password > Change Password > "key icon":
Password Assistant: Numbers only - iOS: If using iCloud Keychain, it's possible to set a
Strong Password
when creating a new web account; how strong? how easily edited/replaced?
Apple: Automatically fill in strong passwords on iPhone
Change PIN for Phone, Tablet
- And:
Settings > Location and Security > Screen Lock: Pattern: drawing pattern; weak, if simplePIN: 8+ digitsPassword: 24+ alphanumeric iOS:
iOS: Settings > Passcode > Change Passcode >[on right: iPhone]
Passcode options:Custom Alphanumeric Code: e.g., iPad: 5+ word phrase or 24+ charactersCustom Numeric Code: e.g., iPhone: 8+ digits6-Digit Numeric Code: (weak)- When travelling or leaving device unattended, there's no 'Lock Screen' command (like macOS)
that forces a passcode prompt upon next wakeup. Some options... - How to Hard Lock an iPhone to Prevent Unauthorized Biometric Access
for Face ID equipped iPhones: Press and hold the Power button and either Volume button
for about 2-3 seconds; OSXD; 9/1/2022 - ~4 unrecognized fingerprint attempts: use a different finger from the ones used to train Touch ID.
- Power down iPhone/iPad, restart.
Generate Memorable Passphrase for Computer, Password Manager, etc.
- For some devices and accounts, a strong but easily 'typable' password
(all lowercase, numerals) may be desirable, e.g., -

Password Strength by XKCD is licensed under a
Creative Commons Attribution-NonCommercial 2.5 LicenseWi-Fi router access for your guests
(or provide scannable QR code) - Netflix streaming credentials via keyboard menu on smart TV
- During system startup, login to user account,
system services, e.g., iCloud (AppleID),
or app, e.g., Dropbox,
-- before password manager is accessible - A few web sites block autofill or paste
(supposedly to increase security?)
-- thus requiring manual entry of credentials,
via typing or clicking onscreen keyboard,
e.g., treasurydirect.gov. - It's difficult to think up a long, unique
passphrase yourself -- use a generator
to avoid common phrases, lines from poems,
movie titles, Bible quotes, etc. - e.g., "correct horse battery staple"
[on right: XKCD cartoon]

via Wikimedia Commons,
Creative Commons Attribution 3.0 Unported
Generate Passphrase: Diceware
- Diceware -- or diceware-like generator in PM or OS
- Roll 5 dice to select a word from a list of 7776 (65) words in some language,
e.g., English word list (EFF discussion); lists in other languages. - Repeat to add another word.
- Stop when phrase is long enough.
 Generate Passphrase: PM
Generate Passphrase: PM
- 1Password: Memorable/Words: # words, separator, etc.
[on right: iPad; below right: Mac]  Optional: to increase strength even more, customize generated words,
Optional: to increase strength even more, customize generated words,
e.g., mixed case, digits, punctuation*, misspellings,
reversals, acronyms, invented words, other languages;
*hackers already anticipate simple 'leet' substitutions like $ for S, 1 for L, etc.
if including 'unusual' chars (accented, foreign, etc.) ,
check availability / compatibility / keyboard for cross-platform use,
e.g., unlocking password manager on different devices
Generate Passphrase: OS
 macOS:
macOS: System Preferences >
Users & Groups > Password >
Change Password > "key icon"
[on right: Mac]> Password Assistant : Memorable
note: missing in newer macOS versions? [below right: Mac]- Longer phrase: generate & concatenate two!
Change Passphrase for Desktop Computer
 macOS [see screenshots above, right]
macOS [see screenshots above, right]- macOS:
(apple) > Lock Screento require a password immediately,
e.g., if leaving computer or travelling - Understanding macOS lock screen options ApIn; 5/7/2023
- Win:
Settings > Accounts > Sign-in Options > Password > Add/Change
 Complex (Pastable) Character Sequences for Web sites, Apps
Complex (Pastable) Character Sequences for Web sites, Apps
Generate Sequence: PM
- 1Password: Random / Characters:
# chars; symbols; numbers/digits
[on right: iPad, Mac]  "Avoid Ambiguous Characters" omits easily confused chars: 1 / I, 0 / O;
"Avoid Ambiguous Characters" omits easily confused chars: 1 / I, 0 / O;
useful for typable passwords [available only in some versions?]
Generate Sequence: OS
 iOS: see Apple: Automatically fill in strong passwords on iPhone
iOS: see Apple: Automatically fill in strong passwords on iPhone
(using iCloud KeyChain)- macOS includes a Random option with its Password Assistant:
- macOS:
System Preferences > Users & Groups > Password >: length (31*) [on right: Mac]
Change Password > "key icon": Password Assistant :
Random - *for longer password: generate & concatenate two!
- Your OS may offer to generate and store passwords for a browser, e.g., Chrome, Safari,
and maybe sync securely online, e.g., iCloud Keychain - This can be convenient (and free), but generally not as secure
or full-featured as a dedicated password manager,
especially if your device/computer has a weak password
-- or you've left it logged in when you step away!

is licensed under CC BY-NC-SA 2.0
Other Generation Methods
- Physical methods can take time;
simple substitutions easy to crack;
e.g., Wikipedia: Secret decoder ring [images on right] - 'DiceKeys' Creates a Primary Password for Life with One Roll
new kit leaves your cryptographic destiny up to
25 cubes in a plastic box -- cute, but unnecessary; Wired; 8/21/2020 -

Captain Midnight decoder badge
by Sobebunny
via Wikimedia Commons
is licensed under CC BY-SA 3.0Use this Rubik’s Cube-style device to create ultra-secure
computer passwords video: The Ultra Password Cube; 4/24/2018 - App/site -- how random? options? dictionary size?
risky if it surreptiously logs the new passwords; these sites might be ok:
webfx.com;
random.org;
privacycanada.net;
xkpasswd.net (based on XKCD cartoon: correct horse battery staple);
privacycanada.net;
Molis Hai -

"crosspassword: correct horse battery staple"
by Steve Weyer
based on Password Strength by XKCD
generated at: armoredpenguin.com"crosspassword" -- a term I coined as a joke);
free-form crossword-like "2-D password" puzzle created from a passphrase [on right]
as a "password" it's weaker than original 1-D passphrase, i.e.,
less random due to "crossings" of entries; the clues give away the words! ;-)
P@s$w0rdz: Testing Passwords
P@s$w0rdz: Testing Passwords
Measuring Strength | How Strong Should Your Passwords Be? |
Information Entropy | Tester: zxcvbn
 Measuring Strength
Measuring Strength
- Your passwords are probably weaker than you think -- you can test below.
- Different web sites might evaluate the same password differently:
Poor / Good / Excellent labels and 'strength gauges' are inexact/relative. - A password manager generally assesses password strength accurately.
 Perhaps your OS offers a built-in tester, e.g. macOS Password Assistant.
Perhaps your OS offers a built-in tester, e.g. macOS Password Assistant.- Like password generators, password testing apps / sites may be safe -- or not.
- Obtaining an "information entropy" value can provide more confidence
about a password's strength -- and unpredictability.

is licensed under CC BY-NC-SA 2.0
How Strong Should Your Passwords Be?
- Current recommendation: passwords should have 'high' entropy: 75+
- zxcvbn entropy scores and 'cracking times' are estimates.
- Password breaches are ongoing, hackers learn new tricks,
and processing speed continues to increase. - "Future proof" your passwords (to some extent) by making your passwords
even longer and stronger than seems necessary now. - It doesn't "cost" anything using a PM to create and enter strong passwords
even for seemingly unimportant sites -- why not? - A few random passwords generated by 1PW, with E values from zxcvbn (v 4.4.2):
- 4-word random phrase: E= ~78 -- lengthen or modify for esp. important passwords
- 5-word random phrase: E= ~94 -- strong enough?
- 64 random chars: E = ~212 -- no need to test
- 100 random chars: E = ~330 -- no need to test
max permutations = RL
E = log2(RL)
E = log2(10'guesses_log10')
E = 'guesses_log2(bits)'Information Entropy (Math Alert!)
- Longer, more complex passwords are stronger -- no surprise -- but how much stronger?
- R: the Size of character set (# of possibilities): 0-9, A-Z, a-z, punct.!, dictionary list -- larger is stronger
- L: to the power of the Length of password sequence (number of characters / words) -- longer is stronger
- E: Information Entropy is related to the number of possible 'permutations'
('combinations' where order does matter): - the log function yields "bits of entropy" -- a more manageable (smaller) number than total permutations
- guesses_log10, guesses_log2 are estimates from zxcvbn tester (covered below)
- entropy is decreased by recognizable words / patterns, e.g., 12345, pet/sports names, popular phrases/quotes,
keyboard sequences, etc. and cracked password lists -- common is weaker, since hackers usually try these first - Higher entropy means less predictable, i.e., more attempts / time to guess or crack by brute force
Tester: zxcvbn
- My favorite strength tester zxcvbn provides an entropy value with annotations.
- zxcvbn is trustworthy since it's open source code;
also, zxcvbn does not log passwords; however, if you're concerned,
turn off internet access after loading page to run locally. - demo zxcvbn form: click below demo label to highlight input field; enter a password to test;
E = log2(10'guesses_log10'); in Google:log2(10^guesses_log10) - Compare old and new zxcvbn algorithms: includes log2 calc;
E = 'guesses_log2(bits)'
P@s$w0rdz: Storing Passwords
P@s$w0rdz: Storing Passwords
Paper, Memory, etc. | Browser: Autofill; Apple: Keychain; Cookies |
Single Sign On | Encryption: Local, Cloud

by Dianna Geers is licensed under CC0 1.0
Memory; Tattoos; Paper; File; Password Manager
- "Never memorize something...
- Reused and weak passwords are the easiest to remember,
especially if you have many accounts. - Unfortunately, these are insecure and might be forgotten.
- You could setup strong passwords for only "important" accounts
-- but how to decide which ones to protect and
which to abandon eventually to hackers? - Why clutter your brain with remembering all of those passwords,
plus generating new unique ones? -

"Password Book 1 005" by ronijj
is licensed under CC BY 2.0It's better if you can limit recall to several strong (memorable) PINs and passphrases:
- one for each device
- one for an encrypted file or password manager (PM) app
- With tattoos, you'd always have your passwords with you. ;-)
- If visible, they're public.
- If ink is temporary, passwords could wash off.
- If ink is permanent, passwords would be difficult to update.
- Paper can be a workable option if you don't mind entering long, strong passwords,

"How to not keep passwords safe"
by European Parliament Technology - DG ITEC
is licensed under CC BY-NC-SA 2.0storing them somewhere secure, and keeping a backup copy.
- If you store passwords in a text document or spreadsheet,
is file strongly encrypted,
and does device have a strong password? - You'd need to manually sync file between any devices,
generate strong random passwords via your OS or browser,
copy/paste from document into web pages,
and remember to close document when you're not using it. - But, if you don't need a PM's convenience or other features,
a file -- if strongly encrypted (later discussion) --
would be a simpler, less expensive alternative to a PM - We'll be focusing on Password Manager apps in upcoming sections.
- Regardless of your storage medium -- memory, paper, file, password manager, ...
-

"Hiking Club Password Sign, Wild River State Park"
by Tony Webster is licensed under CC BY 2.0Will you -- or someone you trust (but not hackers) -- be able to access your accounts
- if you die, or your memory fades, or there's a fire, flood or burglary?
- So, securely and remotely backup any passwords, esp. for devices & password manager,
e.g., device you evacuate with, cloud service, Safety Deposit Box, and/or a trusted friend - 'The Wallet Event': Crypto Startup Bankrupt After Losing Password to $38.9 Million Physical Crypto Wallet the company also did not write down recovery phrases; 8/26/2023
- How to prepare your digital assets in case of death MW; 10/21/2020
Browser
Autofill
- Many browsers will offer to save passwords, along with credit cards, addresses (contacts), etc.
and later "autofill" like a password manager. -

Authorization by XKCD is licensed under a
Creative Commons Attribution-NonCommercial 2.5 LicenseAlthough free and convenient, it's not as portable or fully featured as a password manager.
- How secure is your system software and device password? Device unattended or unlocked?
- Malicious apps and browser extensions might be able to access those passwords.
- When ready to install and use a password manager,
if a browser is saving passwords, avoid confusion/interference later:
1. export existing login entries from browser
2. remove passwords, credit cards and contacts from browser
3. disable browser autofill - 1. export existing login entries as .csv table;
there may be an option to import this file directly into a PM;
when done importing, remember to delete the file (it's not encrypted) - macOS*:
Safari > Passwords > (...v) > Export Passwords - How to Import and Export Passwords From iCloud Keychain to Other Password Managers
*requires macOS 12 (Monterey); LH; 10/29/2021 Firefox > Preferences > Privacy & Security > (...) [top right] > Export logins- Export login data from Firefox Lockwise
Chrome > (:) [3 dots far right] > Settings >
Autofill > (:) [3 dots] > Export passwords- 1Password: Move your passwords from Chrome to 1Password
- Google: Manage Passwords
- How to Export and Delete Saved Passwords in Microsoft Edge
- 2. remove autofill entries from browser
- macOS:
Safari > Preferences > AutoFill >
User names and passwords; Credit cards: Edit - iOS:
Settings > Safari > AutoFill >
Names and Passwords; Saved Credit Cards - iOS:
Settings > Accounts & Passwords: edit Firefox > Preferences > Privacy & Security >
Logins and Passwords: Saved Logins;
Form and Autofill: Saved Addresses, Credit Cards- Win:
Edge > Settings > View Advanced settings >
Autofill: Save Passwords/Cards: Manage - Save or forget passwords in Microsoft Edge
- Google: Manage Passwords
- 3. disable browser autofill
- 1Password: Turn off the built-in password manager in your browser
- macOS:
Safari > Preferences > AutoFill >
User names and passwords; Credit cards: off - iOS:
Settings > Safari > AutoFill >
Names and Passwords; Credit Cards: off - iOS:
Settings > Accounts & Passwords: edit Firefox > Preferences > Privacy & Security >
Logins and Passwords: Autofill: off;
Form and Autofill: Autofill: off- Win:
Edge > Settings > View Advanced settings >
Autofill: Save Passwords/Cards: off - Save or forget passwords in Microsoft Edge
- Google: Manage Passwords
- Why your browser's password manager isn't good enough
browser-specific; mobile support? less robust than standalone PM; PC; 1/25/2021 - Refs: Browser (as PM); Chrome; Edge; Firefox; Safari
 Apple: Keychain
Apple: Keychain
- "Passwordless" passkeys were discussed earlier.
- This term is somewhat misleading since device accounts and web sites still require passwords,
but the OS would store and manage your passwords, with no separate password manager app required. - The "primary password" would generally involve possession of another device,
authenticated via biometrics (fingerprint, face) on phone, watch, etc. - However, you would still need to provide a device password occasionally.
- The same earlier caveats apply.
- Keychain may work only for Apple devices
-- and maybe only with the latest (upgraded) OS versions (Passkeys requires iOS/iPadOS 16+; macOS 13+)
and only for some browsers (e.g., Safari, Chrome but not Firefox?) - You still need strong device passwords for iCloud/AppleID, Mac, iPad and/or iPhone
-- the scheme is only as secure as the weakest password. - You need to lock/logout device when away,
to avoid access to your account, already logged-in sites, password resets, etc. - If you follow these caveats and need no other PM features,
Keychain (plus Passkeys if available) could provide a free, convenient, secure PM alternative. - Re-enable Safari Autofill (above)
- To enable Keychain syncing:
- macOS:
(apple) > System Preferences > Internet Accounts > iCloud: Keychain (on)  iOS:
iOS: Settings > (user) > iCloud: Keychain (on)- To view / edit credentials (User Name, Password, Website):
- macOS:
Safari > Preferences > Passwords - iOS:
Settings > Passwords & Accounts > Website & App Passwords - To see notifications about compromised/weak passwords:
- iOS:
Settings > Passwords > Security Recommendations > Detect Compromised Passwords - If you do use Safari & iCloud for passwords, and have recent devices,
you could use iCloud's new 2FA capability instead of a separate 3rd-party app. - How to Use Hide My Email for Signups from iPhone & iPad OSXD; 10/14/2021
- You Should Use Your iPhone's New Built-in Two-Factor Authentication
only iOS15, macOS 12? LH; 9/23/2021 - How to take control of your passwords using iCloud Keychain on your iPhone, iPad, and Mac
While iCloud Keychain is safe, secure, and easy, it's also very tied to both our Apple devices and Safari in general.
There’s no easy way to export passwords, sync notes, share passwords with other browsers, or access your keychain
on an Android phone or Chromebook; MW; 2/15/2021 - How to use Apple's Keychain password manager in Google Chrome TNW; 2/1/2021
- How to share a password via AirDrop from iOS 14, iPadOS 14, or macOS
from KeyChain, even if iCloud syncing off; MW; 10/23/2020 - Refs: iCloud
Cookies
- On login page, a site may offer some options:
e.g., "remember me", "stay logged in", "trust this device" and/or "not require 2FA/MFA codes"
-- such choices store a browser cookie (like a claim check) to identify your device and browser. - If you have a weak password on your device or a long delay before password is re-requested,
a thief could access your browser and some sites without a passsword, MFA code and/or 'secret answer';
malware might also be able to steal & reuse your browser's cookies. - A Password Manager can quickly fill-in securely-stored credentials: username, password, MFA code.
- So, leave those site options unchecked -- and periodically clear cookies (next).
- It's a good practice to logout when you're done especially for sensitive sites.
It's easy to login again later with PM. - To clear all cookies (sites will require login next time):
- macOS:
Safari > History > Clear History and Website Data(cookies, history, other data) - macOS:
Safari > Preferences > Privacy > Cookies and website data >
Remove All Website Data - macOS:
Firefox > History > Clear Recent History - macOS:
Chrome > Preferences > Advanced Settings > Privacy > Clear Browsing Data - iOS:
Settings > Safari > Clear History and Website Data(cookies, history, other data) - For more details, see section: Safer Internet: Browsing: Manage Storage of Private Data: Cookies

is licensed under CC BY 2.0
Single Sign On
- Generally, don't login to 3rd party sites using your Facebook / Google / LinkedIn / Twitter
credentials -- aka Single Sign On (SSO) or "Oauth" or "Federated Identity" - From a privacy standpoint, you may not know which information
you're allowing sites to share, e.g., contacts, emails, tracking, etc. - From a security standpoint, it's like using the same password across sites -- a no-no;
anyone with access to your device could access those sites. - If one site is hacked, you can be vulnerable on multiple sites that use those same credentials.
- If you change the password or change your mind,
did you keep track of which sites for which you'd need to revoke or update authorization? - An exception: "Sign in with Apple" appears to address these issues
-- though it may not be as widely available yet; Sign in with Apple FAQ MW; 4/8/2020 - no tracking; random email address with free anonymous forwarding; requires MFA
- Still, you'd probably be better off with a Password Manager -- or Passkeys (eventually).
- Refs: SSO (Single Sign-On)
Secure (Encrypt) Your Passwords
- Summary: If you use a strong key, e.g., primary password,
with latest software versions using AES encryption standard
-- preferably AES-256, but AES-128 is still excellent --
passwords (or other info) are the most secure,
whether stored locally or in the cloud. - Some apps that use AES-256:
- 1Password (and most password managers)
- Office, Acrobat (productivity apps)
- WinZip, 7-Zip, Keka (compression utilities)
- And there are others, but you need to check the fine print.
- Interested in more details about security of older app versions,
symmetric vs. asymmetric encryption,
local vs. cloud security, and other tools -- read on. - Below: main encryption methods, and corresponding examples of Local and Cloud storage,
ranked by security: 0 (none/weakest) - 2/3 (strongest); my characterizations/estimates; disclaimer: I'm no crypto expert - Strength of encryption and level of protection correlate to strength of device/primary/account passwords,
encryption algorithm (RC vs. AES), and number of bits used (AES-128 vs. -256).
 Symmetric vs. Asymmetric Encryption
Symmetric vs. Asymmetric Encryption
- symmetric: same cryptographic key used
for both encrypting & decrypting; best for single user;
how to communicate key separately and securely to someone else? - examples (using AES-256):
password manager/vault: 1Password;
disk encryption: FileVault (Mac), BitLocker (Win);
cloud backup: Backblaze;
other apps, e.g., MS Office, Acrobat, WinZip; 7-Zip; Keka
-- generally, long-term file protection - Wikipedia: Symmetric Key e.g.,
Advanced Encryption Standard (AES), 128-, 192-, 256-bit;
use the same cryptographic keys for both encryption of plaintext and decryption of ciphertext;
for communication, requires secure initial exchange of one (or more) secret keys between the parties - How does AES encryption work? 2/4/2019
- asymmetric: several different keys involved (some known by each party);
user encrypts with own private key & server's public key;
server decrypts with own private key & user's public key (-- and vice versa);
more points of vulnerability: software regularly updated on both user and server? certificate authorities - examples: web: https:; email: IMAP, SMTP -- generally, short-term communication
- Info encrypted only during transit between user and server using TLS (asymmetric)
- Info decrypted and generally stored decrypted; it may be re-encrypted by server,
e.g., sending email to recipient, or storing sensitive info, e.g., credit cards;
passwords possibly encrypted, but converted to "hashes" (instead of plain text, hopefully) - Any already-encrypted files preserve original encryption, e.g., 1Password, 7-Zip
- End-to-end encryption (E2EE) -- between users, without server decrypting/re-encrypting
-- is possible/desirable, but difficult to achieve, e.g., really secure chat. (Governments hate E2EE). - Wikipedia: Public Key aka asymmetric cryptography; e.g., Transport Layer Security (TLS), SSL,
S/MIME, PGP, and GPG; requires two separate (but mathematically linked) keys,
one of which is secret (or private) and one of which is public;
public key (certificate) is used to encrypt plaintext or to verify a digital signature;
whereas the private key is used to decrypt ciphertext or to create a digital signature;
computationally infeasible for a properly generated private key to be determined from its corresponding public key - Wikipedia: symmetric vs. asymmetric: postal analogy
- Fact Sheet: Does quantum computing put our digital security at risk?
symmetric vs. asymmetric; # of qubits; Internet Society; 7/2021 - Refs: Be Safer on the Internet:Encryption
- Not all encryption is the same or necessarily strong!!
Local Encryption: computer, phone, tablet
- 0. [none] unencrypted file or passwords/credit cards in browser -- anyone with device password
or with access to internal (unencrypted) drive - 1. [older; symmetric]; weakly encrypted file (text, spreadsheet, .pdf, etc.); oldest software
- Windows: Why You Should Never Use the Native .Zip Crypto in Windows; instead, use AES, e.g., 7-Zip, Office, etc.;
macOS: ctrl-click (Archive) and zip (Terminal) have poor encryption; instead, use AES. i.e., Keka, DiskUtility, Office, etc. - [DES; RC4-128, ?]: Microsoft Office (95-2003), Adobe Acrobat (6.0-), WinZip (2.0-);
Apple iWork, Preview (-2016?); OpenOffice? - [Blowfish]: LibreOffice (-3.4)?
- 2. [AES-128; symmetric]; moderately encrypted files/folders; older software
-- Office (2007-2013), Acrobat (7.0-), WinZip (9.0-); Apple* (iWork): Pages, Numbers; Preview (2016?-)
*Security of Password-Protected iWork Documents bottom line: AES-128 is very secure ('centuries' to crack vs. 'millenia' for -256);
still, since FileVault and Disk Utility already support AES-256, why hasn't Apple increased default encryption for apps (backward compatibility?) - Pages/Numbers/Keynote:
File > Set Password - Preview:
Export > Encrypt [checkbox] - 3. [AES-256; symmetric]; strongly encrypted
via latest software with strong primary password or private key: - password vault; e.g., 1Password
- selected files, e.g., Office (2016-; 365-); Acrobat (X, Pro DC); LibreOffice (3.5-)
Microsoft Office encryption evolution: from Office 97 to Office 2019;
LibreOffice password-protected files; 3.5 (AES) vs. earlier encryption - Word:
Tools > Protect Document - Excel/PowerPoint:
File > Password - Adobe Acrobat Reader/Pro* DC:
File > Property > Securityor
Edit > Protection > Security Properties-- *Reader: check-only (free); Pro: change ($)
> Show Details: Encryption-level - How to Password Protect Any File
Microsoft Word, Excel, and PowerPoint; Google Docs, Sheets, and Slides; Apple Pages, Numbers, and Keynote; Wired; 6/19/2022 - LibreOffice:
File > Save as > Save with Password.odf: metadata not encrypted; .pdf - files/folders w/ compression: WinZip (9.0-); 7-Zip (Win; free);
Keka (7-Zip on Mac; site: free; App Store: $3) - entire device: phone/tablet: e.g., Android, iOS -- anyone with device passcode
- folder / disk partition, e.g., Disk Utility (Mac) into .dmg file
 entire disk, e.g., FileVault (Mac) or BitLocker (Win):
entire disk, e.g., FileVault (Mac) or BitLocker (Win):
-- if private key (pk) is saved in PM, it's accessible only by you;
if pk saved in device's keychain/registry, anyone with device password?
if pk saved in cloud by OS, anyone with cloud account password or subpoena?
Remote Encryption: server, cloud [TLS; asymmetric only during xfer]
- 0. unencrypted public file/folder on cloud storage
-- anyone with URL can typically access - 1. unencrypted private file/folder on cloud storage;
also received/sent email still stored on email server;
-- anyone with account password; cloud provider? accessible by govt. subpoena? - 2. [AES-128; symmetric] separately encrypted
via latest software with strong primary password / private key: - selected files: Apple iWork: Pages, Numbers, Keynote; Preview on cloud storage
- 3. [AES-256; symmetric] separately encrypted
via latest software with strong primary password / private key: - password vault: e.g., 1Password
- all files/folders: e.g., Backblaze (cloud backup service)
- selected files: Office, Acrobat Pro, LibreOffice, WinZip, 7-Zip, Keka
on Box, Dropbox, Google Drive, iCloud, Microsoft OneDrive, ...;
P@s$w0rdz: Password Managers
P@s$w0rdz: Password Managers
Intro | Pricing | Recommendations | Getting Started |
Security | Accessing Sites | Organization
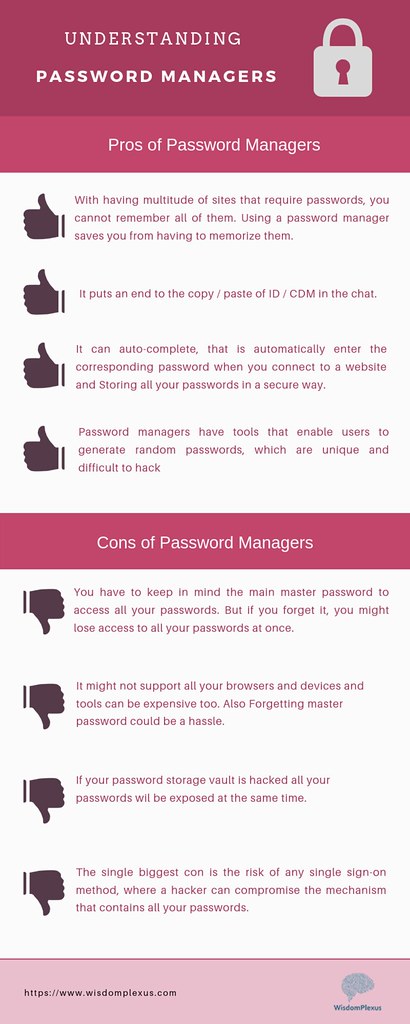
by wisdomplexus is licensed under CC BY-SA 2.0
Introduction
- "One Ring to rule them all." ~Lord of the Rings
- "Passwords are one of the primary pain points in our modern digital existence."
~Why You Need a Password Manager - From the course intro:
- "Reduce stress and declutter your brain by remembering just 1 primary password;
a "password manager" app can store, encrypt and fill-in all of your online logins;
in particular, I will demonstrate 1Password (mostly on the Mac & iPad)." - "The menus and commands for 1Password on different platforms
(Android, ChromeOS, iOS, Linux, Mac, Windows) and browsers
should be almost identical in user interface and functionality." - "For other password managers, the concepts and features should be very similar,
but students will have to locate the analogous menus and commands themselves." - Disclaimers: ever-changing versions & features,
user interface & platform differences, pricing, ...
-- and of course reviewers' biases, and users' preferences & working styles.
Features vary over time between browser extensions and full apps. - Current versions (9/18/2023): macOS 11.7.10; iOS 15.7.9 (iPhone) -- 1Password 8.10.16;
iOS 12.5.4 (iPad) -- 1Password 7.10.2 - Screenshots (~2021): macOS 11.5.1; iOS 14.7.1 (iPhone), 12.5.4 (iPad) -- 1Password 7.8.6
- Screenshots and command sequences here differ from later versions.
- Behavior may change after PM and OS updates and for different web sites!
- Which features? How to choose: # of positive reviews? security?
company reputation? platforms? price? Steve's opinion? - Five reasons why you need a password manager
1. Browser Integration; 2. Password Generation; 3. Phishing Protection;
4. Cross Platform Access; 5. Surveillance Safeguard;
plus debunking these beliefs: "I'm not a target.";
"I already have a perfectly good system for managing passwords.";
"If someone steals my password file, they have all my passwords.";
"I don't trust someone else to store my passwords on their server."
Pricing
- Pricing depends on number of users, number of devices, features, ...
- Free. Most PMs offer free trials;
some offer free versions, but with limited features or support - Purchase. Software license for each user and/or device? major upgrade more $?
currently, most PM vendors promote subscriptions; 1Password no longer offers individual licenses. - Subscription. Plans usually include software licenses, updates, upgrades,
support and cloud storage. # users? #devices? - Some PMs offer Business plans -- not covered here.
- A Family plan enables users to share some password entries in a shared vault -- or directly with other users;
remaining entries for each user are stored in a separate private vault, each with its own primary password.
May support primary password recovery for and emergency access to other accounts. - If all family passwords can be shared in a single vault with the same primary password,
and login entries for same site are differentiated with labels or tags for each user,
sharing an individual plan may suffice (and save $1-2/mo.)
Top Recommendations
- Most often mentioned and rated highest: 1Password (1PW), Bitwarden, Dashlane
- Available for all major OS platforms: Android, iOS, Mac, Win, ChromeOS, Linux;
some even support Apple watchOS, e.g., as token to unlock vault, display MFA codes, etc. - Supported for all major browsers: Chrome, Edge, Firefox, Opera, Safari; others?
- Pricing below for subscriptions (monthly rate if billed annually); free trials available.
- 1Password [developer: AgileBits]
- Individual: 1 user, all devices; $3/mo.
- Families: 5 users, all devices; $5/mo.
- 25% first-year discount [last checked: 5/6/2023];
Tidbits members get 6 months free - Tutorials ; Videos; Refs; Take Control of 1Password (ebook)
- BitWarden [open source]
- Personal: 2 users share 1 vault, unlimited devices; free
- Premium: Personal plus other authentication/security features; $0.83/mo.
- Family: Premium, for up to 6 users; $3.33/mo.
- Help; Refs
- Dashlane [developer: DashLane]
- Individual: 1 user, 1 device, 50 passwords; free
- Advanced: 1 user, 2 devices, unlimited passwords; $2.75/mo.
- Premium: 1 user, all devices; $5/mo.; incl.: VPN, cloud storage
- Family 10 users, all devices; $7.50/mo.
- Support; Refs
- In addition to the Top 3 (1Password, Bitwarden, Dashlane), there are many other password managers,
some free, some with additional features/services, others more limited, less polished, security problems, e.g.:
Dropbox Passwords; Enpass; iCloud Keychain (only Apple devices, discussed earlier);
KeePassX ; Keeper; LastPass; NordPass; Password Boss; RoboForm; Sticky Password - These are discussed and reviewed in the ebook: Take Control of Your Passwords;
see also: Refs: Product Reviews / Comparisons - LastPass? Some who've taken my course may wonder why I no longer recommend LastPass.
- LastPass has had several serious data breaches, including actual password vaults.
- Although LastPass vaults are encrypted, it's possible that they might be cracked someday
-- providing hackers access to all of your accounts. - Given their track record, I lack confidence in LastPass's ability to prevent/minimize future breaches.
- If you'd prefer to use LastPass, I recommend that:
- you change your main ('master') password on any vaults
- you change the passwords on any important accounts, e.g., email, financial,
and use multi-factor authentication when available and secret answers to security questions. - you continue to monitor news about future security breaches
- you consider migrating to a different password manager
 Getting Started: Some Initial Steps
Getting Started: Some Initial Steps
- Select a password manager to try out
-- at a minimum, make sure it's available for all your devices and preferred browsers;
price: usually 30-day free trial; discounts often available: special, or for annual plan - 1Password (1PW): Support; Refs
- Take Control of 1Password (ebook)
- Tutorials: general, Android, ChromeOS / Linux, iOS, Mac*, Windows
- *install from 1Password's own "Password Store": Get the 1Password apps
or Apple's Mac "App Store" [on right]?
same version, but 1Password Store version may offer prompter upgrades,
more flexibility for subscription upgrades/downgrades? it's possible to change versions later:
How to install the 1Password app from 1Password.com after installing it from the Mac App Store - Videos: general; ChromeOS / Linux; Mac
- 1PW videos from enthusiastic users: Getting Started 5:18;
Beginners Guide To 1Password 27:20;
Why 1Password is the best proprietary password manager 27:19 - Refs: Other Product Reviews / Comparisons
 Download and install PM app from App Store for your first device's OS ,
Download and install PM app from App Store for your first device's OS ,
or the vendor's site: e.g., 1Password, BitWarden, Dashlane
[info above for 1Password; on right: after installation, macOS Launchpad: 1Password app icon]- Which device to start with?
- A desktop or laptop is easiest for adding/updating accounts initially,
especially with its display and physical keyboard. - A tablet would be next choice;
less integration in iOS/iPadOS 14 (or earlier) due to system constraints
-- means more switching between PM and browser. - A smartphone will work but it will take longer to enter passwords,
due to its smaller onscreen keyboard and display -- especially if < iOS 15. - Finally, whichever device you start with, you can install PM
on another device later and sync passwords between them.  If you're not using Safari or have a 2nd browser,
If you're not using Safari or have a 2nd browser,
install browser extension for Chrome, Edge, Firefox- Either Get started with 1Password in your browser or
1Password (app) > Install Browser Extensions
displays page to download official extension from the browser's "extension store" - 1Password 8 implements the Safari extension via a separate app:
"1Password for Safari" in Apple's App Store - A browser extension is more convenient than the full app for most common functions.
 The extension and app share access to the same vaults,
The extension and app share access to the same vaults,
so you can create or update a login entry from either.- Make sure the extension is enabled in your browser, e.g.,
Safari > Preferences > Extensions[top right]- 1Password: Safari in iOS & iPadOS 15

Firefox > Tools > Add-ons and Themes > Extensions[above right]Chrome > More (3 dots) > More tools > Extensions- If 1Password browser extension successfully installed,
 a small icon appears in browser tool bar area,
a small icon appears in browser tool bar area,
e.g., Safari [above right], Firefox [on right] - Some possible installation-related issues:
- Updating 1Password itself -- while it's still open, i.e., "Quit 1Password Completely"
- Incomplete install
- Browser extension can't connect to the app
- You may need to reboot.
- To avoid multiple apps intefering with each other when saving your logins:
- Disable any other password manager, you were using,
i.e., in browser settings where you just enabled 1Password (above) - If any browser was saving passwords ('autofill'),
export existing login entries from browser, remove entries,
and disable autofill, see earlier Browser: Autofill section;
also: 1Password: Turn off the built-in password manager in your browser  Individual or Family plan -- do you need to keep passwords separate?
Individual or Family plan -- do you need to keep passwords separate?- Simplest to start with Individual plan (1 user); you can upgrade to Family later if desired.
- Setup an account -- usually cloud subscription
- Create and save primary password -- at least an initial one;
you can replace it with a stronger one later. - Save "private key" (extra security) if provided
-- store in PM, and create emergency kit [on right], e.g., for SD box.
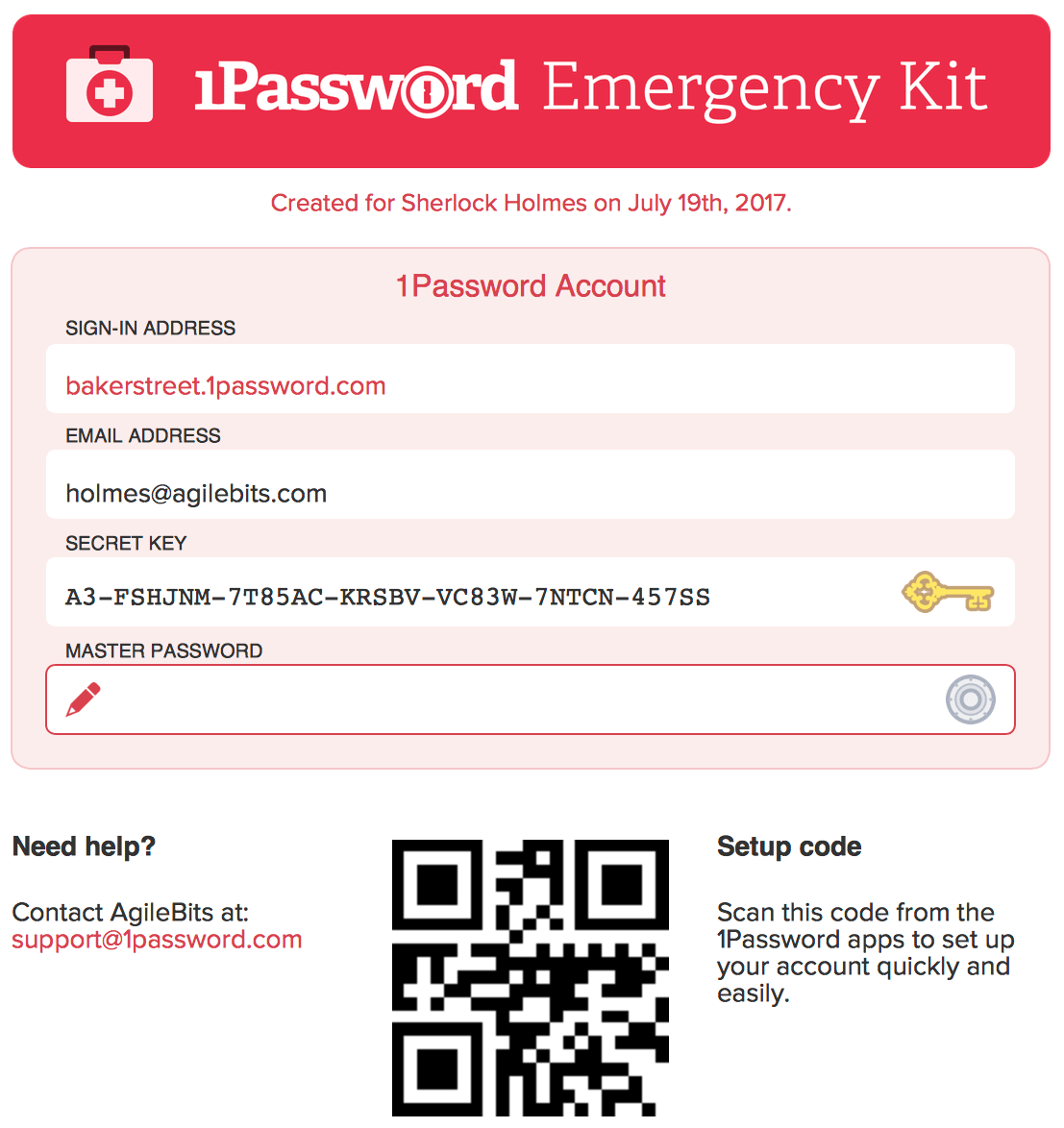 1PW Emergency Kit is also useful for setting up 1PW on other devices.
1PW Emergency Kit is also useful for setting up 1PW on other devices. - 1PW video: Sign-up for 1Password
- 1PW videos: To migrate existing 1Password entries from an app
to a subscription (1password.com) account: iOS; Mac; Windows - Optional: if you had been using another password manager,
or used your browser to save and autofill logins -- and you had exported them,
you can save setup time by importing these entries into your new PM. - 1Password: import from other PMs or spreadsheet

1Password > File > Import: (format)[on right]
remember later to delete or encrypt any files with passwords remaining outside the PM!- You can also import .csv (comma separated values) on 1password.com web site (where you setup account)
- Specify whether file contains Logins, Credit Cards or Secure Notes;
e.g., for logins, indicate which columns contained title, username, password, URL, notes (if any) - Pick some less important sites to start with / practice on.
- When you login to a site for the first time,
if 1Password does not yet have your username and password,
you need to enter these from memory or from a scrap of paper or... - 1Password should display a prompt offering to Create New or Update Existing login entry.
 If no prompt appears, e.g., some sites not recognized or in older iOS,
If no prompt appears, e.g., some sites not recognized or in older iOS,
manually create entry:1PW (app) > File > New Login:
Title; username, password, website (home or login URL)- If login or password update failed, click "Not Now" and try again
- Click "Update Existing" to list existing logins for that site;
if you changed the password successfully, select an existing login entry from the list to update;
if none listed or it's a new account, add a title and click Create New. - With subsequent logins to that account, 1Password should autofill.
- Other ways to see which login entries (accounts) have already been added:
- the popup menu lists accounts when you click on a password or username field in a login form for a site
- browser extension lists entries for the current domain, or enter a name, e.g., "OLLI" in the search box
 As you change a password on a site,
As you change a password on a site,
PM should offer to update existing vault entry;
section:P@s$w0rdz: Updating: How (includes manual updates)- 1PW video: Change your passwords and make them stronger
- Explore features; re-read more sections here;
 vendor sites: FAQs, tutorials, videos, support articles/forums
vendor sites: FAQs, tutorials, videos, support articles/forums - Add / update more sites...; section: P@s$w0rdz: Updating: Strategy
- Stronger primary password?
[below right: Mac:1Password > Preferences > Accounts > Change Master Password] ??? - Install PM on another device? [on right: 1Password in iOS App Store]
- Configure PM on new device
[below right: Mac:1Password > Preferences > Accounts > Set up other devices];
1PW Emergency Kit (form) [earlier image] is useful both as backup and for setting up other devices. - Give yourself a pat on the back, sleep better at night,
and enjoy your PM whenever you login to or manage a site.  How to Get Your Family to Actually Use a Password Manager
How to Get Your Family to Actually Use a Password Manager
start small with secure sharing of popular accounts, such as streaming services or news subscriptions;
set up a shared document with crucial info for your executor/heirs;
extra protection (MFA) for your email, financial info, health info;
subscription family password manager vs. individual plan vs. more technical hands-on solutions;
leverage finances, budgeting, and other life skills; incentives? be persistent; Wired; 10/5/2021
 Security
Security
- One of the major reasons you'd want a password manager.
- Your very strong, memorable password -- known only by you (not even by PM vendor)
encrypts (AES-256) all passwords (and other info) in a secure vault on your device and/or cloud. - Local vault still accessible, even without internet connection.
- Sync/backup vaults securely between devices,
usually via 1Password cloud account -- safe, since vault still encrypted;
older versions of 1Password may still support sync via other cloud services,
e.g., Dropbox, iCloud, ... or manually (no cloud): WLAN (Wi-Fi) - 1PW tutorial: Sharing vaults with your family
- Move/copy items between different vaults: 1PW video; 1PW tutorial
- Backup of vault probably not necessary if using cloud sync;
however, backup at least the primary password & device passwords
that you're remembering, e.g., safety deposit box, trusted friend in their PM.  It is possible to export entries from 1Password if you decide to use a different password manager.
It is possible to export entries from 1Password if you decide to use a different password manager.1Password > (pick vault) > File > Export >[right]
Selected/All Items: (format)- Some may want to Print entries on paper or save as a .pdf, perhaps as another form of backup?
- Take special care with sensitive info that's now outside the secure PM
-- in spreadsheet, paper or .pdf form -- by deleting after temporary use, encrypting it or storing somewhere else secure. - What if you do forget your primary password?
- Several password managers (Bitwarden, Dashlane, Keeper, RoboForm) have an emergency access feature;
beforehand, you designate one or more emergency contacts; later, they can gain access to your account;
1Password is working on this feature. - 1Password Families currently supports sharing of your key passwords with other trusted persons.
You can also print out and store an emergency kit. - Travel Mode: Remove (hide) sensitive data from your devices when you cross borders;
restore access with a click when you arrive.  How often do you want to enter your primary password?
How often do you want to enter your primary password? - Convenience vs. security tradeoff: when leaving device or travelling,
lock vault manually, or automatically via timer preference or device sleep. - macOS: 1PW (app):
Preferences > Security: Lock on sleep;(on right)
Lock after computer is idle for __ minutes; etc. - To lock 1Password manually:
- macOS:
1Password (app) > Lock - Win:
1Password (1PW7) | Account Name > Lock 
 To unlock 1Password (besides entering primary password):
To unlock 1Password (besides entering primary password):
Apple Watch, Touch ID, Windows Hello- For iOS, depending on your device model,
you can enable PIN, TouchID, or FaceID
for convenience. - You can force primary password prompt
with incorrect PIN/scan, or Lock Now
-- especially important to do for 4-digit (weak!!) PIN
before walking away from device. - iOS (iPhone7): 1PW:
Settings > Security:(on far right)
Lock Now; Lock on Exit;
Auto-Lock __ Minutes; TouchID - iOS (Pad Air): 1PW:
Settings > Security:(above right)
Lock Now; Loc on Exit;
Auto-Lock __ Minutes; PIN Code - video: Use Touch ID to unlock 1Password on your iPhone or iPad
 Generate & Store very strong, random passwords of different types:
Generate & Store very strong, random passwords of different types:
numbers (PIN), phrases, complex character sequences -- section Generating Passwords- Generate & Store unique usernames, e.g., anonymous, linked email addresses
1PW video: Create Masked Email -- section User Names - Generate & Store Time-Based/Temporary One Time Password (TOTP) codes
-- a more secure alternative to SMS texting; see MFA section - Check for vulnerable, weak, compromised passwords; see Updating Passwords
- Even more secure: 1Password accounts (and Dashlane) support Multi-Factor Authentication.
- If you already have a separate private key, it might not be necessary. It's more complex to set up and use;
the extra code needed might not be accessible from that device's own PM (since you need to login first -- with a code!). - You could use another authenticator app, e.g., Authy, another device,
or a special USB key, e.g., YubiKey to generate the TOTP code.

 Accessing Sites
Accessing Sites
- Saved login credentials may be accessible via several different interfaces.
- 1. Within a page's login form, click on username or password field.
PM offers list of credentials matching that site;
you may need to open PM first with your primary password.
on right: form popups in Mac Safari. - 2. Browser extension (via icon in browser toolbar)
or system extension (via icon in system's menu bar).
 This 'mini-app' provides most of the features you need.
This 'mini-app' provides most of the features you need.
-- on right: Mac mini-app via Safari toolbar.
Before iOS/iPadOS 15, extensions behaved differently from desktop. - video: Use the 1Password extension to save and fill passwords
on your Mac or Windows PC - 3. Regular app, with possibly different user interface and additional features,
e.g., creating secure non-login items; autofill in selected apps (not just browsers); sorting;
persistent local storage; Watchtower access; syncing locked/unlocked state between browsers  Navigate to correct site; automatically fill-in userid and password for most sites
Navigate to correct site; automatically fill-in userid and password for most sites
-- via browser extension or app;- Some situations may require a manual copy/paste step, e.g.:
- entering password into an app (not browser), e.g., Dropbox, Skype, Zoom
- a page containing multiple forms can conflate username & fields
for both new accounts and existing users, and confuse PM; - a form on a page may require other fields,
e.g., zipcode or secret answer to a security question - financial institutions may have multi-page logins, with user name on first page, then password, security questions and/or MFA code on subsequent pages
-- with maybe a CAPTCHA puzzle thrown in. - some sites may unfortunately prevent paste/autofill
-- requiring keyboard or menu - often you can resolve confusion by manually editing the PM's site item
to replace an obsolete login or initial account registration page - You do need to click Login or Submit manually to complete a site's login process.
1Password no longer has an option to "auto-submit" after auto-filling credentials
to avoid security problems, e.g., hackers harvesting credentials from fake login pages.
If your PM has an auto-submit feature, disable it.  If site mismatches domain for account,
If site mismatches domain for account,
e.g., URL typos or possible phishing links, 1PW provides an alert and does not autofill.- Log into PM once, then access many sites easily,
e.g., downloading monthly statements - Login to a site or update password on a site -- PM creates a new, or updates an existing, vault entry
- 1PW video: Change your passwords and make them stronger
- Same login entry works for subdomains, e.g., example.com, xxx.example.com
- Login entry can store multiple URLs using same unique credentials,
e.g., appleid.apple.com, icloud.com - Multiple accounts for same site would be separate entries,
stored in shared vault or different family member's vault,
differentiated by name label, e.g., OLLI Joe, OLLI Jill - You could also associate a local "file URL" with a login entry,
i.e., where on your computer you store monthly downloaded .pdf statements
from that bank, utility, credit card company, etc. - Setup local file URL in 1Password on Mac
Finder: (select folder) > File > Get Info > (select ‘Where’ field contents) > Copy
orctrl-click folder in Path Bar (Finder window bottom) > Copy folder as Pathname1Password > (login entry); Edit- locate last (template) "website" field, say,
website 2: https://example.com/ - replace "website 2" (title) with "Local Archive"
- replace https://example.com/ (value) with folder path, i.e., Paste;
value would look like:/Users/account/Documents/Finance/Bank1/Statements - add
file://at the beginning; value would then look like:
file:///Users/account/Documents/Finance/Bank1/Statements - Save login entry
- Use local file URL
- Login to site and download statement file
1Password: (login entry) > Local Archive (field) > Open and Fillno Fill occurs- New Finder window opens, directly showing the destination path and folder
- Drag downloaded file to that folder.
 iOS/iPadOS
iOS/iPadOS
- For iOS/iPadOS 15, 1Password behaves similarly to desktop version
- 1PW: Getting Started; Safari in iOS & iPadOS 15; Change Website Password
- Older, more limited iOS/iPadOS extensions are discussed in this section.
- Unfortunately, iOS (14 and earlier) doesn't recognize new or changed logins on a site;
add a site: create manually in 1PW app;
update a site: copy/paste info from site entry. - In even older versions of iOS and 1PW app,
you could click on login entry to open site in a mini-browser,
or you could manually copy credentials and switch to regular browser to paste.
These approaches still work but there are more convenient options.  Enable Autofill from browser (via kbd) on iPhone and iPad
Enable Autofill from browser (via kbd) on iPhone and iPad
set up:Settings > Passwords (& Accounts)
> Autofill Passwords > 1Password: enable
use: tap 'key' icon on keyboard to open 1Password -- far right- Use the 1Password extension to fill in Safari and apps
set up:Safari (window) > ('share' icon w/ up arrow)
> Edit Actions > 1Password: enable
use: tap (share icon) to open menu; select 1Password -- near right - Copy and fill passwords into apps that don't work with 1Password
- Drag and drop (via multitasking) to fill in other apps on your iPad
 Organize Logins, Other Info
Organize Logins, Other Info
- Organize / access sites via menu, search, category / tag or favorites
- 1PW video: Organize with favorites and tags on your Mac
- To reduce confusion / improve security,
remove regular browser bookmarks/favorites for any sites requiring login - Store other confidential info, e.g.,
- video: Use 1Password to save and fill credit cards and addresses on your Mac
- videos: How 1Password can replace your wallet; Create passport entry
- 'normal' & 'virtual' credit cards
- 1PW flags cards nearing expiration
 Tag accounts that use that credit card, e.g., "VI-BofA" for autopay and recurring subscriptions
Tag accounts that use that credit card, e.g., "VI-BofA" for autopay and recurring subscriptions
to make it easier to find and update those accounts with new credit card details.- virtual: create/login privacy.com account, linked to a debit card or bank account
- create virtual card for specific account, e.g., merchant; one-off & recurring payments;
- optional: link virtual card directly to 1Password (1PW);
'1Password X' browser extension required for Chrome, Firefox, and Edge;
if 1PW integration not yet available (mobile or desktop apps; Safari browser),
manually copy/paste virtual card from privacy.com into 1PW (or other PM) - How to Pay Using Virtual Credit Cards in 1Password LH; 9/24/2020
- Identities, i.e., contact info (name, address); drivers licenses, passports
- In Login entry's Note or additional fields: secret answers; site password rules; backup/recovery codes, etc.
- In secure Note entry: device password, product model/serial numbers; hard drive encryption key, etc.
- If you forgot your device password, you could access the note from 1Password on a different device,
or from your emergency info (backed up securely elsewhere) where you recorded the primary password for password manager, etc. - Include important files -- each 1Password user has 1Gb of cloud storage on 1password.com
- If your document (or set of documents) would use too much storage,
encrypt the document (using Office, 7-Zip, etc.),
store it locally on your device and/or in another cloud account,
and save a local or cloud link in a secure Note along w/ the document password. - Software installation keys
- Codes for garage, alarm; etc.
- Use a password manager as a "digital will": 1Password
P@s$w0rdz: Updating Passwords
P@s$w0rdz: Updating Passwords
When? | Strategy | How? | Auto-Update? |
Manual Update #1 (macOS) | Manual Update #2 (iOS) |
Exceptions

is licensed under CC0 1.0.
"Somebody figured out my password"
How Do You Know When to Update?
- "Change is the one...
- Just tried to change my password to 'The_Last_Jedi' but...
- If your workplace requires password changes every 90 days,...
-
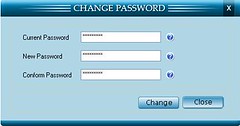
"Change Password" by ppclandingpages
is licensed under CC BY-SA 2.0Change weak and reused passwords
-- and any that may have been compromised in a data breach. - Some sites may require a new password when you try to login;
some sites insist on periodic password changes (obsolete, counterproductive advice);
some sites may have upgraded minimum password requirements;
some sites may have had a recent breach. - You receive an email from site, or read news about account breaches or site hacks.
- You receive an email from site indicating a recent login or password / account change,
"Yahoo passwords hacked" by 1000zen
is licensed under CC BY 2.0or you check 'recent account activity' on site -- unexpected device or location?
- Of course, you wouldn't click on a possible phishing email link,
but instead go to that site directly from your PM. - Check haveibeenpwned.com* w/ username or email for exposed accounts/info
have i been pwned? : 'pwned' (gamers): totally dominated, conclusively defeated - 1Password automatically checks via
Watchtower: Vulnerable - Another site: HPI Identity Leak Checker
- For an exposed site where you have an account, change its password;
After a breach, users rarely change their passwords, and when they do, they're often weaker;
to make things worse, users' new passwords were overall more similar to passwords they use on other accounts - For other sites, e.g., 3rd-party marketing,
you can be angry but not particularly worried;
do you have credit freezes & monitoring in place?  1Password: WatchTower checks for and highlights potential problems:
1Password: WatchTower checks for and highlights potential problems:- Compromised; Vulnerable, i.e., haveibeenpwned.com
- Reused (multiple sites); Weak
- Unsecured Sites, i.e., http: -- passwords, credit card info not encrypted when sent; vs. https:
- Multi/Two-Factor Authentication Avail (TOTP)
- Expiring, e.g., credit cards, passports
- iOS:
1PW > Settings > Security > 1Password WatchTower: on
-- may be limited in functionality, compared to desktop version 1Password plans to upgrade in future;
when examining an individual entry, any relevant warning should appear in Red.
A Password Strategy
- A lot of passwords and accounts? How do I cope, where do I start?
- Apply password triage -- prioritize* by importance, and update a few at a time
- If just learning how to use a password manager, it may be best to practice first
-- with some unimportant accounts, rather than more critical email or financial accounts. -

"Toaster Password cartoon from 'Mr. Brunelle Explains it All'"
by Robert Waldo Brunelle Jr, CC BY-SA 4.0, via Wikimedia CommonsClose any accounts you no longer use
-- then there's no need to save/update. - After login, change password, review password reset procedures;
update secret answers; save recovery codes - Optional: turn on multi-factor authentication (MFA) when available & appropriate
- 1Password:WatchTower can suggest accounts to review:
Compromised, Vulnerable, Weak, Reused, Unsecured, 2FA
*Possible Order [& Type]
- Device(s), Password Manager [Memorable]
- when learning PM: some unimportant accounts for experimentation -- then the important accounts
- Email accounts, esp. any used for password resets [Random/Typable; 2FA]
- Financial institutions; sites that store credit card details, e.g., Amazon, Apple, utilities, etc. [Random; 2FA]
- Cloud backup services, photo storage sites, or any other services that hold especially valuable personal data [Random; 2FA]
- Sites with personal info (address, phone, email); social media, airlines, car rental [Random]
- All others, weakest first [Random]
How to Update Passwords
- Ideally, this process could be simpler and more automatic;
unfortunately, sites have difficult-to-find 'change password' pages
with different steps, and different rules for acceptable passwords. - Remember that the account's password is stored in 2 places:
- 1. remotely: the web site
- 2. locally: your PM 'Login' entry contains username, password, site URL
- So, new password needs to be updated in 2 places:
1) the site -- usually first, since you want to make sure new password has been accepted
2) the PM 'Login' entry -- save the new password to replace previous password - Also, if you're using an app associated with a site, you'd need to update the password
in that app separately later, e.g., Dropbox, Zoom, email client - 1Password: Change your passwords and make them stronger: Mac, Win, iOS, And
- video: Change your passwords and make them stronger on Mac and Win
Auto-Update?
- Several PMs offer a premium ($) feature to automatically update passwords for selected, popular sites, e.g.,
- DashLane: Password Changer; ~500 sites
- This sounds like an attractive feature, but which of your sites does it handle,
how reliable/secure is it, and will complex logins work, e.g., Security Questions or 2FA? - Without this feature or for other sites, you still need to know how to update passwords yourself.

 Manual Update #1 (macOS)
Manual Update #1 (macOS)
- This section describes an update process that's straightforward for many sites,
especially from desktop systems. - The process will vary depending on your OS, PM and site idiosyncracies!
- Exceptions and workarounds will be covered later.

 Go to Correct Site & Login
Go to Correct Site & Login
- open site; find Login button / page
-- use your PM, a browser bookmark or an 'official' search result!
*Do not click on possible phishing links in emails,
or (mis)type the site address - Login to site: autofill, copy/paste or type ('Reveal') password from PM;
if entered from previous source: memory, paper, file, ...,
PM should prompt to Create New entry.
[on right: 1PW login entry: Open & Fill; site page filled before clicking 'Sign In']

 Find 'Change Password' page
Find 'Change Password' page
- This can sometimes be the hardest task since every site is different!
- Where is it: User name/icon; Account; Settings; Profile; Security, ...?
- [on right: menu bar: "My Account"; Account page: Username & Password]
- You could use "Forgot Password" when logging in to reset password
-- with an expected email, it's actually ok to click on that link!
(Of course, without strong device password and timeouts/locks,
hackers with physical access to your locked device could
access your still-logged-in email application,
receive the 'Forgot Password' reset email, and change your accounts passwords).
 Change Password page: Fill-in Old password
Change Password page: Fill-in Old password
- page might include up to 3 fields:
1. old password -- Fill from PM or wait & copy later;
2. new password -- PM generates for you;
3. confirm new password -- PM fills that in too;
if page includes password 'hint' field, leave it blank -- or enter "none". - Fill old password: autofill from PM,
or manually copy/paste password from login entry.
[on right: login page; ready to autofill Old password field from PM entry]
 Change Password page: Generate and Fill-in New password
Change Password page: Generate and Fill-in New password
- Your PM can generate random, strong passwords more easily than you can
-- save your brain for more important things. - One simple option is to "Use Suggested Password" from 1PW's menu [on right]
- Although the suggested password may be adequate and compatible with most sites' rules,
it's not particularly strong -- only ~16 characters long? - Also, this triggers 1PW's update dialog before finding out whether site will accept the new password;
if site rejects it (and you've already saved in 1PW), you may need to recover 'old' (current site) password (View Password History) and try again. - Current suggestion: edit the login entry in 1PW app.
Generate new password of desired type and strength there.
Use (copied to but not yet saved in field); Copy new password to clipboard;
Paste into site's form fields. Submit.
If site accepts password, Save the login entry already containing new password.
If site rejects password, generate a new one and add Note about site's rules for future reference.  [on right: both New and Retype fields filled with suggested password]
[on right: both New and Retype fields filled with suggested password]
Update Password; Success?
- 'Submit' button to update password.
If PM has an auto-submit setting,
that should be disabled for security reasons.  Check that site accepted new password:
Check that site accepted new password:
confirmation message or lack of error message?- [on right: site: "Your Password has been updated";
1PW: pops up dialog to update a login entry] - If site update successful, let PM update login entry with new password.
Update Existing: if more than one existing account, select the correct one;
Create New: create a new account entry. - Site may send an email notification about changes to account information.
- If site update failed, do not approve update of PM's login entry
-- the old password is still in effect on site, and still stored in PM. - Optional: other account security settings, e.g., update recovery and contact info;
change Secret Answers; enable MFA? - Exceptions section will discuss modifying password to meet site requirements,
using stronger or more memorable/typable passwords,
or how to get old password from PM even if you did save the invalid one accidentally,
what to do if PM doesn't notice password update, etc.
Test
- Log out from site, or site may have logged you out.
- Login again using PM. Success? logout; proceed to next account to update.
- Sometimes the site will accept the new password with no complaints,
and the PM updated the correct login entry, but subsequent login fails. - Perhaps the new password was too long, and the site just truncated it rather than warned you.
- Click "Forgot Password" on site's login page to receive a reset link via email,
try updating with a shorter password, and add site requirements to login entry's Note field.
Manual Update #2 (iOS)
- It's easier to update passwords on a desktop system, and now in iOS/iPadOS 15.
- Browser extensions in older iOS (14 and earlier) are not as fully integrated as desktop versions.
- Ideally, the manual update process described earlier works on mobile devices too.
 However on my older iPad with older iOS 12.5.4,
However on my older iPad with older iOS 12.5.4,
other steps were necessary -- described below.- "switch to (app)" = Home button double-tap to access an already-open app
- In 1PW, select login entry
- [on right: login entry; website: Open; or website: Copy]
 Login page
Login page
- Several login options:
- 1. click 'website' to open in temporary mini-browser (not full Safari app)
and auto-fill credentials - Otherwise, Copy website field;
switch to browser: Paste; site menu: "Join"; login page appears. - 2. tap Safari browser bar : 'share' icon (box w/ arrow) at top right; actions appear.
 [above right: action menu includes 1Password (previously added)]
[above right: action menu includes 1Password (previously added)]- [on right: list of suggested login entries appears; pick item to autofill]
- 3. click Old password field; 'key icon' Password should appear above keyboard;
however, key keyboard item did not appear for this site's login page,
but did appear for Change Password page (later) - 4. switch to 1PW: select entry; Copy password;
switch to browser: Paste into Old
Change Password page: Fill-in Old password
- Once logged in, navigate to Change Password page.
 Click Old password field;
Click Old password field; 'key' Passwordsappears above keyboard (this time)- If it doesn't appear, try #1 [share icon] or #3 [1PW entry: copy] (above)
- [on right: 'key' Passwords option]
 Tap 'key' to see 1PW suggestions; select entry to fill Old password field
Tap 'key' to see 1PW suggestions; select entry to fill Old password field- [on right: select 1PW login entry to autofill Old password]
 Change Password page: Generate and Fill-in New password
Change Password page: Generate and Fill-in New password
- Click on New password field -- popup offers no password generator option, unfortunately.
- Switch to 1PW: select login entry, click Edit button (upper right)
- [on right: 1PW login entry with Edit button]
 While editing entry, click gear icon at far right of password field.
While editing entry, click gear icon at far right of password field.- Adjust password length and pattern options.
- Generate a different random password with circular refresh icon at far right.
- Each generated password is copied into the password field.
- Satisfied? click Done button at upper right to save New password in entry.
- [on right: generating a password]
- Note: earlier manual process updated site first, then PM entry;
this process updates the PM entry first, then the site.
If your new password does not conform to the site rules and is rejected,
to try again -- retrieve the old password from the entry's Previously Used Passwords;
see PM, but not site, updated with new password; retrieve old password (below)  Copy the newly saved password from login entry.
Copy the newly saved password from login entry.- [on right: Copy new password to clipboard]
- Switch to browser: Paste into New field(s);
submit change; celebrate!
Exceptions
- This section covers a few special situations.
- Generate a Different Password
- Site, but not PM, updated with new password
- PM, but not site, updated with new password; retrieve old password
 Generate a Different Password
Generate a Different Password
- Maybe the password Suggestion does not conform to the site's rules,
or you want a stronger or more memorable/typable password. - Sites have different length limits, and require / allow different characters.
- Exceed the minimum suggestion / requirement when possible
-- the longer, more diverse and random the better. - [on right: generate random 100-character sequence; Save&Copy to form]
- The generator usually saves new password to system clipboard,
creates a temporary 'Password' log entry containing the password,
and pastes the password into the site's change page New field(s)
(and hopefully not overwrite the Old password field).  Unfortunately, a site might not spell out its rules until after you fail the first time!
Unfortunately, a site might not spell out its rules until after you fail the first time!- In Notes field for PM's login entry, add comments about any length,
character or 'pastability' limitations to make password updates
for that site easier in the future. - [on right: new generated password appears in New and Retype fields]
 Site, but not PM, updated with new password
Site, but not PM, updated with new password
- PM may sometimes fail to recognize
that a password change occurred on some sites. - If the new password is still on the system clipboard,
paste into login entry (see below) . - If you used password generator, another way to access the new password:
- [on right: most recent password generated for the site; Copy]
 macOS/iOS:
macOS/iOS: Categories: Password: (site item w/ 'key icon')- Copy the new password from most recent (see timestamp) Password item
- Edit the site's Login entry; paste into the entry's password field; Save
- 1PW: If you used the password generator and can’t find the password to sign in
- [on right: pasting new password into login entry]

 PM, but not site, updated with new password;
PM, but not site, updated with new password;
retrieve old password?
- If you allow the PM to
update its login entry (which now has New password),
or you had to do this iOS reversed update sequence,
but then learn that the site update failed,
e.g., New password didn't meet site requirements
or site is waiting for you to provide the old password
as final step before completing update: - [on right: Mac: Password History; iPad: Previously Used Passwords]
 To access the old password to redo or verify site changes:
To access the old password to redo or verify site changes:- macOS:
(login entry) : Password field >
("v" far right) > View Password History - iOS:
(login entry) :
Previously Used Passwords (button at bottom) - [on right: Mac: Password History: previous passwords]
P@s$w0rdz: Security Questions & Answers
P@s$w0rdz: Security Questions & Answers
Quotes | The Problem | How to Improve
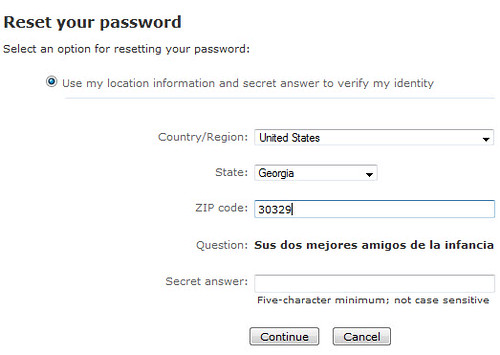
Quotes
- "I don't have a bank account because...
- "The 10 Most Common Password Security Questions...
- Password security questions for the depressed:...
- "Your password should be secret, but...
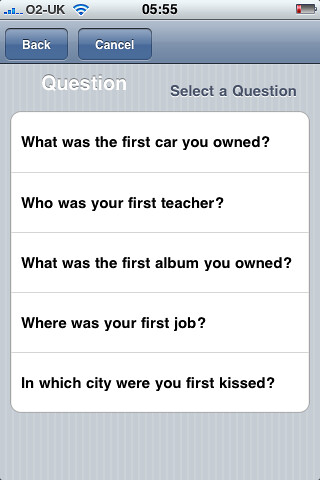
is licensed under CC BY 2.0
The Problem
- Some sites use the answers to security questions as an extra authentication factor.
- These 'secret' answers are often weak, short, guessable, reused on multiple sites, etc. -- illusory security.
- Can you remember what your favorite food or movie was years ago when you created an account?
- Have your interests, preferences or memory recall changed in recent years?
- Hackers may be able to find those answers:
- on social media sites, e.g., best friend in grade school, pizza preference, favorite color, ...
- in public records, e.g., mother's maiden name, street where you lived, ...
- in ongoing data breaches from other sites, e.g., answers and info that are no longer 'secret'

Creative Commons Attribution-NonCommercial 2.5 License
How to Improve
- To avoid a hacker impersonating you and hijacking your account,
reduce personal information available online
and strengthen existing (and new) secret answers. - Reduce posting -- by you and your 'friends'
-- of your (and their) personal details on social media;
added bonus: marketers will know less about you. - Don't participate in quizzes/polls that trick you into revealing personal info!
e.g., Why You Shouldn't Play That 'Fun Quarantine Game' on Facebook
Why Social Media Name Games Are a Security Risk -
"password" by Terrapin Flyer is licensed under CC BY-SA 2.0 Don't supply 'hints' for your secret answer -- or for your password.
- Update any answers for each site to be unique / unpredictable :
- If menu only: choose an untrue, opposite, or weird answer
- Otherwise: enter a misspelled, foreign, false or random phrase.
- If site allows you to create your own security questions,
why not a hacker-proof one? e.g., "What's the answer to Question 1?" -- with a random answer!  Desirable characteristics: (from Choosing and Using Security Questions Cheat Sheet)
Desirable characteristics: (from Choosing and Using Security Questions Cheat Sheet)
Memorable: The user must be able to recall the answer to the question,
potentially years after creating their account.
Consistent: The answer to the question must not change over time.
Applicable: The user must be able to answer the question.
Confidential: The answer to the question must be hard for an attacker to obtain.
Specific: The answer should be clear to the user.- Avoid cluttering your brain.
 Record secret answers -- along with the question -- in PM [e.g., Notes field; on right]
Record secret answers -- along with the question -- in PM [e.g., Notes field; on right]- To be even more organized,
create a "Security Questions" section (this may be automatic in future versions of 1PW),
and add an individual field to separate each question & answer [on right].  When requested, just lookup, copy, and paste an answer.
When requested, just lookup, copy, and paste an answer.- Don't rely on secret answers alone for sensitive accounts
-- use Multi-Factor Authentication when available - Refs: Security Questions
P@s$w0rdz: Recovery & Usernames
P@s$w0rdz: Recovery & Usernames

is licensed under CC BY-SA 2.0
Recovery: Email & Phone Contacts; Backup Codes
- Provide accounts with a 'semi-permanent' (non-ISP-dependent)
email contact address, e.g., icloud.com, gmail.com.
An ISP address can disappear if you move and/or change ISPs. - Optional: provide phone# (voice / text) as a backup contact,
and perhaps 2nd email. Update mailing address? - Facebook Doesn't Need Your Real Phone Number LH; 1/26/2021
- Your primary email account, used as contact,
often as a username for other accounts, is important to protect
-- it's often used for receiving password resets for those other accounts! - Supply a second (backup, semi-permanent) email address
to receive notifications about unexpected logins or password changes
to your email accounts, e.g., primary: gmail & alternate: yahoo;
primary: icloud & alternate: outlook; etc. - Otherwise, if you forgot your primary email password, how could you
access that account, especially any password reset emails? - Since this email account is a "backdoor" into many other accounts,
be sure to access your accounts with encryption, e.g., SSL/TLS,
set all your devices to lock when not in use, and require a strong password to unlock each device. - How to (hopefully) restore your Gmail account if you lose access Verge; 8/4/2021
- If a site provides backup/recovery codes, store in PM, e.g., Notes field
-- this is esp. important if password reset or MFA not avail. - Some services provide legacy & emergency contacts, e.g.,
- Facebook: Trusted Contact, Legacy Contact
- Google: inactive account manager
- 1Password: (family) emergency kit
- Bitwarden: Emergency Access
- 'Semi-permanent' email addresses probably won't disappear, even thru corporate mergers,
e.g., icloud.com, gmail.com, yahoo.com, outlook.com, aol.com, pobox.com
-- and other mail / forwarding providers (many free) - A 'temporary' email address could disappear when you change jobs, finish school,
or change ISPs (by move, necessity or choice),
e.g., your-job.com/.gov/.org/.edu; ashlandhome.net, charter.net, spectrum.net, mind.net,
comcast.net, att.net, ... -- maybe this is less likely for Rogue Valley retirees? - After a temporary email account is gone, could you easily access any account later
that used that old email as a username or contact? - Why ISP email services are terrible, and what to use instead
Apple's iCloud, Google's Gmail, Microsoft's Outlook.com; paid services; ApIn; 5/12/2023 - Why You Should Sign Into All of Your Accounts Every Now and Then
inactive accounts -- inaccessible due to invalid email address;
account deletion -- policies vary: 6 mo. - 2 years; LH; 11/30/2021 - Be Safer on the Internet: Email

"Let's see what's cooking on Facebook.
What was my password -- the Gmail one?
Which was not the one I put on Twitter?
Maybe if I go to Myspace I'll get it back.
It wouldn't let me in. and Blogger? Waiting.
Has my Flickr account expired?
The horror. The horror. I am scattered in chunks
all over the network. and I can't access myself!""
by LuChOeDu is licensed under CC BY-NC-SA 2.0
Usernames
- Create a unique username -- if site doesn't require it to be an email address
or phone number; be sure that PM records it - If site requires an email address as username, use an alias if possible [below].
- If you can't, use stronger passwords, better secret answers, MFA!
- A unique username is more private
-- more difficult for marketers or hackers to identify you by collating data fragments;
a unique email address might suggest who leaked / sold it to spammers and hackers. - It's more secure -- if hackers found that (unencrypted) username in a data breach,
they could access only that site (assuming they'd discovered the password),
but not other sites (with different usernames). - An email address is less desirable as a username since:
- some sites don't allow you to change it later
-- problematic if a temporary email was provided initially; - an email address is not unique (typically) -- so, it's a little less secure/private:
possibility of credential stuffing by hackers & cross-site tracking by marketers. - If you must provide an email address as a username, preferably use:
- 1. aliased email address; some email providers support permanent aliases,
which all route to a primary email address, e.g.,
jsmithMail@icloud.com, jsmithList@icloud.com, jsmithTemp@icloud.com,. => jsmith@icloud.com - Add and manage email aliases for iCloud Mail on iCloud.com -- up to 3 free aliases
- 2. several services generate random email addresses linked to your underlying email:
- Apple: Hide My Email create unique, random email addresses to use with apps, websites;
it's built into "Sign in with Apple" (SSO-like service) and iCloud+ (paid plan) - Use 1Password to create and manage Masked Emails in Fastmail
unique email aliases for logins, much like Apple's iCloud+ Hide My Email function
but integrated w/ 1PW, e.g., when creating new account entries. - Currently requires a fastmail.com account ($2.50/mo.);
1password.com (your account):Integrations > Masked Email > Fastmail: (connect to FM account) - Firefox Relay: generate unique email aliases;
requires Firefox account (free) and use of Firefox browser and Private Relay extension;
some sites may not accept subdomains in address, e.g., @relay.firefox.com;
can't reply anonymously using that address; limit on size of forwarded attachments - The Best Ways to Hide Your Email Address
Gmail: add . anywhere, or +label before @;
Yahoo: create up to 500 aliases w/ text appended;
Outlook: create up to 10 aliases; Apple: Hide My Email;
Firefox: Relay; 5 free aliases; Premium plan for unlimited;
DuckDuckGo: Email Protection; Fastmail + 1Password: Masked Email;
others: Protonmail, SimpleLogin, Addy.io; Giz; 11/23/2021 - 3. semi-permanent email address; e.g., gmail.com, icloud.com, etc.; pobox.com forwards to another address;
in addition some services allow "+" (or other punctuation) for extended addresses,
which route to main email, e.g., jsmith+facebook@gmail.com, ... => jsmith@gmail.com;
this may provide some uniqueness, and spam filtering;
however, some sites might limit punctuation in email usernames, e.g., allow only . and @. - 4. temporary (ISP) email address (as last resort),
e.g., if you switch ISPs later, will you still be able to access that account and/or change its username?
note: for single-use accounts or email list signup, some temporary email aliases might be ok: Using Disposable Contact Info,
Disposable Email Addresses: Sign in with Apple, 10 Minute Mail; Guerrilla Mail; Burner Mail; Firefox Private Relay;
Disposable Cell Numbers: Burner
P@s$w0rdz: Multi-Factor Authentication
P@s$w0rdz: Multi-Factor Authentication
Introduction | Identity | How does MFA work? |
Setup: Email or SMS | Setup: TOTP (app)

is licensed under CC BY-NC 2.0
"Don't rely on passwords alone to protect anything you value.
Turn on multi-factor authentication (MFA) wherever possible"
Introduction
- Different usernames and random secret answers provide some protection.
- Use a more secure authentication factor in addition to a password,
especially for important accounts, e.g., financial, email
-- or for most accounts if you're a high-profile user. - Generally, a stronger second factor is a time-based (temporary) code
-- provided via SMS (texting), 'authenticator app' or physical token - Terminology for and implementation of this factor varies across sites
-- "Multi-Factor Authentication" (MFA) seems to be the latest preferred term,
but 2-Factor Authentication (2FA) and 2-Step Verification (2SV) commonly appear.
Other acronyms appearing below: SMS, TOTP, QR !! - Microsoft: 99.9% of compromised accounts did not use multi-factor authentication
Only 11% of all enterprise accounts use a MFA solution overall; ZD; 3/6/2020 - A Dutch security researcher says he logged into Trump's Twitter account
using the password “maga2020!” the account has now been secured w/ 2FA; 10/22/2020
-- with slightly different capitalization, this is also apparently the password for the Wi-Fi at Trump rallies. - Trump Twitter 'hack': Police accept attacker's claim BBC; 12/16/2020

is licensed under CC BY-NC-SA 2.0
Identity: Credentials & Authentication
- Credentials: "The combination of your username and password.
In some cases, additional pieces of information, such as your ZIP code
or the answers to security questions, may be considered part of your credentials
-- it's whatever a site or service needs to reliably identify you
as the authorized user of a given account." - Authentication: "The act of proving your identity to a computer system
-- typically by entering your credentials and having them confirmed as
matching the previously stored record." ~Take Control of Your Passwords - Authentication factors:
- knowledge ("something you know"): strong password remembered
or retrieved from a secure place; secret answers -

"Amazon AWS MFA Token Macro - 1"
by ChrisDag is licensed under CC BY 2.0possession ("something you have"): card, phone, physical token/device
- inherence ("something you are"): biometrics; fingerprint; facial recognition;
handwriting/typing/movement patterns; iris scan - The distinction between two-step verification (2SV)
and two-factor authentication (2FA) sounds straightforward: - 2SV: two credentials, e.g., password ('know') and secret answer ('know')
- 2FA: two different kinds (factors) of credentials, e.g., password ('know') and fingerprint ('are')
- However, there can be subtle differences, and sites may not use the technically correct label.
- We'll use MFA' generically here to refer to these; next: more detailed examples.
- single-factor authentication (SFA): e.g., password ('know') or biometrics (fingerprint, face; 'are')
- two-step verification (2SV), e.g., bank login: password ('know') and secret answer ('know')
-
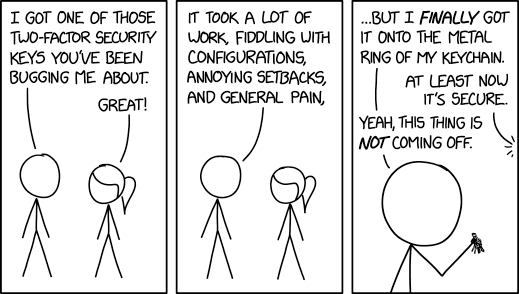
Two-Factor Security Key by XKCD is licensed
via Creative Commons Attribution-NonCommercial 2.5two-factor authentication (2FA), e.g.,
bank ATM: card ('have') + PIN ('know') or fingerprint ('are');
bank login: password ('know') + time-based code ('have')
-- some consider this 2SV ('know') if a hacker can intercept SMS message
or thief can access your device (texts, email, authentication app) - "While two-step verification (2SV) merely expands
single factor authentication (SFA) by requiring
two distinct verification occurrences of one authentication factor,
two-factor authentication (2FA) requires two occurrences,
each under a different category of credential."
~Two-factor authentication (2FA) versus two-step verification (2SV);
[authentication flowcharts]; Multi-factor authentication (MFA)
How Does Multi-Factor Authentication (MFA) Work? SMS, TOTP
- To increase security, you could receive a one-time time-based (expiring) code:
- 1. Sent from site via SMS (Short Message Service) text message to your phone
or email to your phone/computer. - 2. Sent from site via internet to a device/app, e.g., Facebook app, popup on 'trusted' Apple device
-

"Yubikey USB 2FA U2F Security Token"
by Tony Webster
is licensed under CC BY 2.03. TOTP (Time-based One Time Password) generated locally by authenticator app,
e.g., 1Password, Authy, Google Authenticator, Microsoft Authenticator - or by a physical security token, e.g., Yubikey
considerations: site support, browser support, hardware port connector; we won't be covering hardware keys - Locally generated TOTP codes are in sync with the codes expected by the requesting site.
- In addition to text/email, some sites can provide a code via voice call.
- If you don't see your preferred delivery method,
check if there's a link/button: "I need more options".  Enter (type or paste) this code into browser or device prompt
Enter (type or paste) this code into browser or device prompt- Security impact: someone with your password,
but without the time-based code,
would not be able to login from an unknown device. - Allow your browser, only on your private devices, to 'remember' via cookie:
your username and/or that you've been "trusted" (don't ask for MFA again) ? -

Never Told Anyone by XKCD is licensed
via Creative Commons Attribution-NonCommercial 2.5Although it seems like more work to provide userid, password and MFA code
each time you login, it's actually quite easy to autofill or paste from a password manager.
It's safer to always require MFA and never to reveal the code to others. - If you do forget to uncheck the box, you can later remove cookies to reset this 'permission'.
- Summary of possible common credential combinations -- from least to most secure:
- none: no or weak password
- SFA (single factor; know or are): PIN or fingerprint/face
- SFA (single factor; know or are): strong password
- 2SV (know/know): strong password + strong secret answer
- 2FA (know/have): strong password + code via SMS or email
- 2FA (know/have): strong password + TOTP code via authenticator app,
non-SMS app (Apple,Facebook) or hardware key - 2FA is not available for every site.
- It may be named or implemented in different ways.
- If you enable MFA/2FA, take note of how/where in case you want to disable it later.
 Sites that support 2FA: twofactorauth.org Categories:
Sites that support 2FA: twofactorauth.org Categories:
Backup & Sync; Banking; Betting; Cloud Computing; Communication;
Cryptocurrencies; Developer; Domains; Education; Email; Entertainment;
Finance; Food; Gaming; Government; Health; Hosting/VPS;
Identity Management; Investing; IoT; Legal; Payments; Remote Access;
Retail; Security; Social; Task Management; Transport; Utilities; VPN Providers;
e.g., Apple(iCloud), Dropbox, Google/Gmail, Facebook, Microsoft(Live),
Paypal, Twitter, Yahoo- Some sites provide backup codes,
-- useful if no phone or coverage, e.g., international travel;
or a recovery key in lieu of secret answers -- useful if phone stolen/lost;
e.g., AOL, Apple, Dropbox, Evernote, Facebook, Github, Gmail, Live - Store any recovery codes or backup key in PM
- Other fallback strategies: email, voice call, other SMS phone,
authenticator app -- or, disable MFA before a trip, re-enable afterwards. - It's useful to 'tag' login entries in PM, e.g., "MFA-SMS", "MFA-TOTP"
-- to find existing MFA accounts before getting rid of a phone,
setting up a new device, or considering a trip. - If you enable MFA for some sites where you use a separate app, especially email,
you may need an "app-specific password" (ASP) to allow the app to bypass MFA. - The site generates and manages ASPs
-- not your PM, though you could use PM to store ASP, and later copy into app manually.
Each site does things differently. In some cases, you may need a separate app, e.g., Comcast. - If the ASP is weaker than your regular password, or the setup process is complicated,
it might be better to have a strong regular password and not use MFA for that site. - Your "Application-Specific Passwords" Aren't Application-Specific How-to Geek; 11/2/2014
 Setting Up MFA via Email or SMS
Setting Up MFA via Email or SMS
- Email is a possible method to receive codes;
more available than SMS when travelling internationally?
no auto-extraction of code like SMS on Mac;
if device lacks strong password, SMS is better, TOTP (next section) best - SMS texting is the most common MFA method (and better than nothing),
but you may not have your phone, or there's no cell service,
or a phone number could be spoofed, or text messages intercepted;
in addition, providing a phone# can be a privacy leak on some sites,
e.g., Facebook, Twitter (which sell your info to marketers)  SMS on some sites may require U.S.-only phone #.
SMS on some sites may require U.S.-only phone #.- Apple-only? If using WiFi and cellular via WiFi,
iPhone might receive some SMS while travelling (even internationally) - If iPhone # is linked for AppleID, text messages can appear
in Messages app on other devices; - In many cases, macOS/iOS can extract MFA code
from text message; in iOS, code appears at top of keyboard;
in macOS, it's on clipboard to paste into Safari. - Link iPhone & iPad/Mac for Phone & Messages:
- Apple: Messages; Messages on Mac
- Apple: Make and receive calls on your Mac, iPad, or iPod touch
- Apple: Make and receive phone calls in FaceTime on Mac
- Cell carriers often set an account PIN to control changes to your account;
PIN may be set by default to last 4 digits of your SSN -- not exactly secret - A different PIN should prevent stealing of your phone # -- "SIM card hijacking";
contact customer support before a hacker does; record new PIN in Login entry for cell account. - Beware of phishing: some hackers provide email links to fake login pages,
which can capture not only your password, but also your time-based MFA code;
open & login to the correct page using your PM - If a text message with MFA code appears on your locked phone screen, consider disabling these notifications;
otherwise, someone with your stolen phone might be able to access your account
using the publicy visible MFA code, even without knowing your phone's passcode! - iOS:
Settings > Notifications > Messages > Show on Lock Screen: off - If supported, set up a 2nd phone number to receive code, e.g., spouse, in case you can't access primary phone,
e.g., Amazon, AOL, Apple, Chase, Evernote, Github, Gmail, Live, Paypal, Vanguard, Yahoo;
for some sites, if this 2nd phone is already associated with another account, it'll be unlinked, e.g., Facebook  Some sites send the code via a different secure communication protocol
Some sites send the code via a different secure communication protocol
(not SMS or email), though idiosyncratic.- Apple sends MFA code directly to 'trusted devices' (with same AppleID) via popup
- Some sites, e.g., Facebook, can send code to their own proprietary app.
 Setting Up MFA via TOTP in an Authenticator App
Setting Up MFA via TOTP in an Authenticator App
- Using TOTP (Time-based One Time Password)
is preferable to SMS text messaging and email
-- even though fewer sites support TOTP,
and it's a little more complex to set up & use.
Finding TOTP Sites
 Example sites: Amazon, Backblaze, Dreamhost, Dropbox, Evernote, Facebook,
Example sites: Amazon, Backblaze, Dreamhost, Dropbox, Evernote, Facebook,
Github, Google/Gmail, Instagram, LinkedIn, Microsoft(Live.com),
Paypal, Tumblr, Twitter, Uber, WordPress- for more, see: twofactorauth.org: "software token" label;
authy.com: "compatible with Authy" icon - 1Password also flags sites that support MFA;
some, e.g., eBay, may support only own app, and not general authenticator apps
-- add tag "2FA" to ignore/hide.
Authenticator Apps
- Example apps: 1Password, Authy, Bitwarden, Google Authenticator, Microsoft Authenticator
- Authy is a good choice for a separate app, with its multiple-device support and encryption.
- Some authenticator apps may require you to set up everything again if you upgrade to a new phone
-- Google Authenticator has recently added syncing capability;
if no encryption added, security of generated TOTP codes is only as strong as the device password. - Recent Apple devices can store/access 2FA settings in iCloud:
You Should Use Your iPhone's New Built-in Two-Factor Authentication
alternative to 3rd-party app; only iOS15, macOS 12? LH; 9/23/2021  1Password provides integrated support for "One-Time Passwords",
1Password provides integrated support for "One-Time Passwords",
so no separate authenticator app is needed.- 1Password:
(login item) > Edit > Label [...]:
One-time Password; scan QR/copy seed > Save - There are usually two methods for authenticator app & site to initialize and synchronize:

 1. Scan QR ("Quick Response") image provided by a site using a 'scanner window' [on right]
1. Scan QR ("Quick Response") image provided by a site using a 'scanner window' [on right]
or a device camera to initialize 'code generator'- 2. Copy an initial text 'seed code';
[far right]
paste into the authenticator app. - After Save, both app and remote server
will generate the same synchronized
sequence of random codes;
each code expires after a short interval.  To verify initially and to use after setup: enter or copy/paste code from authenticator app into site prompt;
To verify initially and to use after setup: enter or copy/paste code from authenticator app into site prompt;
countdown timer icon indicates how soon code will change (usually every ~0:30).- Upon logging into a site, 1PW copies TOTP code to clipboard,
allowing you to paste MFA code into browser (not apps?) w/o transcribing;
if you wait too long, display Login entry, Copy TOTP code, paste - If you later disable MFA for a site, remember to edit that Login entry:
remove One-Time Password field (for TOTP) and any MFA tag to avoid future confusion;
it's unclear if backup codes are invalid (and if they'd be requested);
if you re-enable MFA later, replace any old codes.
TOTP Setup Examples
- MFA setup process for each site is somewhat different, unfortunately.
- Start/practice with "less important" sites first, e.g., social media
- For email sites especially, be sure to have backup email & phone contacts in place.
- After you're comfortable, tackle more critical sites, e.g., finance,
and sites with more complex or multiple device dependencies, e.g., gmail, AppleID - These examples support TOTP (preferred); some may also support SMS:
- 1Password:
(Account) > More Actions... >
Manage Two-Factor Authentication Settings
1PW does not appear in 1PW's own list of sites that support MFA!
1PW TOTP setup needs to be stored in separate authenticator app, e.g., Authy -- not 1PW itself;
is this complexity worth the extra security? is site access already adequately protected by "secret key"? - Adobe:
Manage Your Account > Password and security >
Manage 2-Step Verification - Amazon:
Your Account > Login & Security >
Two-Step Verification (2SV) Settings - AppleID (Apple):
Security > Two-Factor Authentication - Backblaze:
Account > My Settings > Two-Factor Verification - BestBuy:
Account Settings > Account Security > Manage 2-Step Verification - Dropbox:
Account > Settings > Security > Two-step verification  Facebook:
Facebook: Settings > Security and Login >
Setup Extra Security > Use two-factor authentication:
Text Message, Code Generator (TOTP), Recovery Code- Google:
My Account > Sign-in & Security >
Signing into Google > 2-Step Verification - Instagram:
Settings > Privacy and Security >
Edit Two-Factor Authentication Setting - Intuit:
Account > Sign In & Security > Two-step verification - Linkedin:
Account > Login and security > 2-Step verification - Live (Microsoft):
Account > Security > more security options - Paypal:
Account > Security > 2-step verification - WordPress:
(Account) > Security > 2-Step Authentication - Zoom (Pro; paid account):
Admin > Advanced > Security > Sign in with Two-Factor Authentication - Refs: 2-Factor Authentication / 2-Step Verification