Quotes | Why? | How? | Hackers; Credential Stuffing |
Types: Memorable or Complex |
Remember? | Before Jumping In

is licensed under CC BY-NC-ND 2.0
Quotes
- During a recent password audit, an OLLI student
was found using the following password:
"MickeyMinniePlutoHueyLouieDeweyDonaldGoofySacramento"
When asked why such a long password, the student replied... - "Passwords are like underwear:...
- "This is my password," said the King as he drew his sword...
- Passwords for really forgetful people:...
- Login incorrect....
- "I was going to change my password to be one of my favourite places in France...
- Rick Astley's guide to password management...
- A teenager at a funeral asks the priest for...
- Set your wifi password to 2444666668888888...
- A man needs WiFi at the local pub and asks for the password.
The bartender replies: You need to buy a drink first...
- An IT guy goes to the dentist.
Dentist: Have you been flossing regularly?...
 USER: I can't get on the Internet.
USER: I can't get on the Internet.
SUPPORT: Are you sure you used the right password?...
- Normal people use their...
- "49 Across: It may require letters, a number and a special character...
- Clean water is like your password...
- "I got asked to leave karaoke night for singing 'Danger Zone' 7 times in a row...

is licensed under CC BY-NC-SA 2.0
Why (Strong) Passwords?
- "Passwords are one of the primary pain points
in our modern digital existence."
~Why You Need a Password Manager - Until a more effective, secure and reliable
form of authentication appears,
passwords are a necessary evil -- for now. - Strong passwords can prevent access
to our financial and personal information
by criminals and unethical governments. - Even if you think a site is unimportant,
it may store some personal info
with more added in the future. - If you reuse the same password on other sites
and one of them is hacked, the attacker could
log in as you on all your 'throwaway' sites
and piece together your data fragments
for a more complete dossier about you. -

Authorization by XKCD is licensed under a
Creative Commons Attribution-NonCommercial 2.5Passkeys (discussed earlier) might eventually replace the need for many passwords.
However, they may work best currently for recent devices from one vendor
-- perhaps only with the latest (upgraded) OS versions,
and only for some browsers and accounts/sites. - You still need strong device passwords for computer, tablet and/or phone
-- passkeys are only as secure as the weakest device PIN/password. - You need to lock/logout device when away,
to avoid access to your account, already logged-in sites, password resets, etc.
[on right: general problem for all OSes & devices]
What Makes a Password Stronger?
-

"How to choose a password" by thewikiman
is licensed under CC BY 2.0"To put it simply, a good password is one that you won't forget
[or can copy] but that no one else (human/computer) can guess."
~Joe Kissell, Take Control of Your Passwords - Unique: don't use the same password on multiple sites
-- or a password anyone else has used! - Hackers add passwords from compromised sites to their
lists of leaked credentials then use credential stuffing (below),
hoping that someone reused that password for other sites - Check if a site has been breached for your username(s):
1Password:Watchtower, haveibeenpwned.com
-- update that account, and any accounts with the same password - Linkedin Scraped Data Breach example:
email from haveibeenpwned; 10/2/2021,
update from LinkedIn; 6/29/2021 - Don't log into 3rd party sites with your Facebook
or Google credentials ("Single Sign On") -- more later. - Uncommon: avoid 'obvious' ones and public info,
e.g., names of pets, sports teams, single dictionary word,
keyboard pattern, popular quotes, worst 25 of 2017, etc. - Unpredictable: don't "strengthen" a weak password like everyone else, e.g.,
"Numbers? You'll likely add a "1" at the end.
Capital letters? You'll capitalize the first letter.
Special characters? Frequently exclamation marks."
~Rules for strong passwords don't work, researchers find CNet; 11/12/2020 - The Password Game will make you want to break your keyboard in the best way
Game; Ars; 6/28/2023 - A compilation of sites with dumb password rules
-
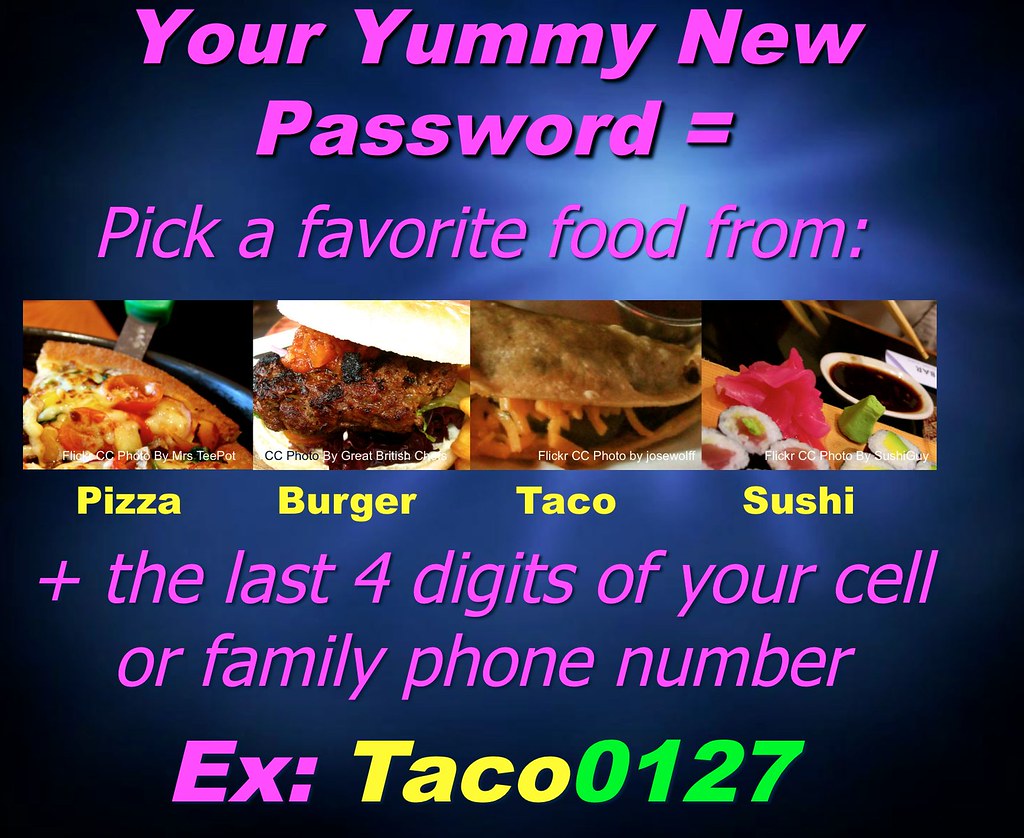
"Yummy Student Password Matrix"
by The Daring Librarian
is licensed under CC BY-NC-SA 2.0Avoid predictable patterns, i.e., a 'base password' combined with a sitename (or its abbrev.),
e.g., "olli-facebook123"?
Could a hacker having that password and inferring a pattern,
guess similar passwords, e.g., "olli-amazon123", "olli-gmail123"? - Password Bingo uses same key/pattern on different bingo cards
to generate/lookup a password -- cute, but insecure if hint includes card# - Unchanging: despite obsolete advice, passwords don't usually need to be changed
unless they're weak, reused or compromised -- though some sites will still insist. - Never Change Your Password
1. If it's sufficiently strong; 2. If you created a unique one for each account;
3. Unless there's a security breach where it's stored; TB; 3/5/2022 - Long: the longer, the stronger: 24-100 characters
- Attackers don't bother brute-forcing long passwords, Microsoft engineer says
77% of attempts used a password between 1 and 7 characters. over 10 characters in only 6% of cases;
only 7% included a special character; 39% actually had at least one number;
none included white space; 11/22/2021 -

Account Problems by XKCD is licensed
via Creative Commons Attribution-NonCommercial 2.5Complex: add (unusual) punctuation, in addition to upper/lowercase, digits
-- if valid for site and typable on your device's keyboard. - Hackers know about appending the same symbol many times,
e.g., ".....$$$$$$$$$", known as "haystack" technique
-- the length increase provides illusionary strength. - Hackers substitute similar-looking numbers or characters,
known as leet (or “1337”) technique
-- so, "P@s$w0rdz" (course title) is no stronger than "Passwords",
nor is "p455\/\/0rd", etc. [below right: $nakesOnAPlane isn't strong] -

""Secure password of the week"
by Simon Lieschke is licensed under CC BY-NC 2.0Complexity is great, but may be more difficult to type
-- longer is more important if you can't autofill or paste or have to remember it. - Unknown: a strong password is worthless if revealed / shared.
- Olympics Broadcaster Announces His Computer Password on Live TV video; 7/26/2021
- The Advanced Spellchecker in Chrome and Edge Saves Everything You Type
-- Even Passwords LH; 9/20/2022 - Or revealed via insecure software or careless user or company practices (details: Be Safer on the Internet);
see also: Steps to Simple Online Security good overall summary 4/1-4/15/2022 -

from: takecontrolbooks.com
Take Control of Your Online PrivacySummary below:
- Install latest software&security updates for operating system,
applications and browser extensions. - Set strong memorable password / PIN for device user account to protect files,
information, contacts, etc.; extra credit: encrypt storage and backups - Use password manager to navigate to the correct site.
- Enter passwords only on official, secure (https) pages.
SSL/TLS (Secure Sockets Layer/Transport Layer Security) encrypts web and email - Don't click on links in phishing emails;
hovering over a link may not popup true destination;
avoid shortened URLs to access login / form pages;
don't log into fake sites aka "social engineering" - 2023 cyber-attacks targeted a vulnerability in the MOVEit filesharing technology
used by many federal & state agencies and corporations around the world.
This breach exposed personal information of millions of people,
including social security numbers in many cases. - Take advantage of any credit monitoring service that your bank or financial institution offers;
set up proactive credit freezes (prevents others from opening a credit card or taking out a loan with your SSN)
and/or deal with identify theft -- see Safer Internet: Identify Theft, Credit Freeze - You can "thaw" all of the credit freezes temporarily later if you do want to apply for credit.
- Don't share passwords (or other sensitive info) via email
- If you must share, consider more secure transfer methods, e.g.,
- How to share a password via AirDrop
from KeyChain, even if iCloud syncing off; MW; 10/23/2020 - 1Password 7.9 Adds Secure Password Sharing;
blog.1password.com; one-use or expiring link,
optional email verification; TB; 10/19/2021 -
"That awkward moment when someone's staring at
your keyboard while you're typing your password."
by QuotesEverlasting is licensed under CC BY 2.0Limit any password sharing to less important accounts,
e.g., streaming services may allow sharing without revealing actual password,
or use MFA (Multi-Factor Authentication) to protect account-level changes - Don't enter password / PIN while anyone is looking at your screen over your shoulder,
or when using others' or public devices since those might contain malware, i.e., keyloggers - Prevent / remove malware on devices you use.
- Connect to Wi-Fi via strong typable password -- encrypted WPA2 (or WPA3).
Otherwise, hackers can "sniff" for username/password combinations
as they’re sent from unencrypted (http:) pages on your computer to a server;
if strong W-Fi encryption not available, use a VPN?;
also set strong admin password for your router. - Reinforced: passwords-alone are often not secure enough; later sections:
-
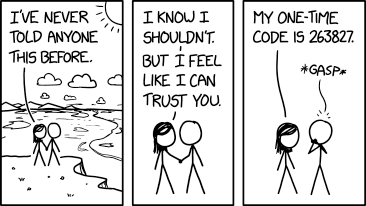
Never Told Anyone by XKCD is licensed
via Creative Commons Attribution-NonCommercial 2.5 - Usernames
- Multi-Factor Authentication (MFA) temp codes via SMS text message or authenticator app.
Have browser prompt for MFA code each time
-- saved authentication cookies can be stolen from browser or intercepted in transit.
Don't provide your MFA codes via phone/text to fake customer support.

is licensed under CC BY-NC 2.0
How Hackers Find Passwords
-- or Credential Stuffing Explained
- Don't use the word "EGG" for your password...
- In an attempt to deter computer hackers I've changed all my passwords to 'Brazil Nut'...
- A (seemingly) alarming news article
-- especially since many of us have used Zoom: - Credentials for 500,000+ Zoom accounts are being sold
on the dark web and hacker forums
Threat actors attempt to login to Zoom using account credentials
[usernames, passwords] leaked in older data breaches. The successful logins
are then compiled into lists that are sold to other hackers; BC; 4/13/2020 -
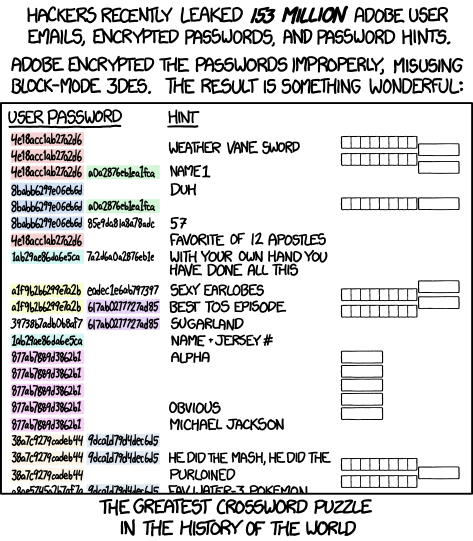
Encryptic by XKCD is licensed under a
Creative Commons Attribution-NonCommercial 2.5 LicenseShould you be worried? change password? uninstall Zoom?
switch to another product (with same or different privacy & security issues)? - Summary: Zoom wasn't hacked.
If a user had created a new Zoom account
with a password reused from a different site (now breached)
or phished from a fake Zoom email & site,
a hacker can easily login into that account
-- unless user had quickly changed the password, or enabled MFA - Curious about why this isn't a Zoom-specific issue,
and the roles of companies, users, hackers -- read on.
Companies
- Some companies have sloppy server & IT practices:
old insecure web/database software, poorly paid/trained staff,
weak/no password protection for sensitive files, etc.
-- attacks on their sites can lead to data breaches
(see Hackers below) -

"Top 500 Passwords" by mkandlez
is licensed under CC BY-NC 2.0Most companies provide client (user) software
with security bugs, or missing or misconfigured
privacy or security features / settings
-- when these problems are discovered,
some companies may be slow to offer software fixes,
or deny/ignore/downplay the problem. - Although many client issues emerged with early users,
Zoom promptly and frequently issued software client updates;
there have been no apparent server problems
-- so, what's the cause of the credentials scare (above)?
Users
- Many users create accounts with the same userid/username,
either because it's simpler to remember,
or sites require using an email address
-- and many users may have only one email. -
"password problems" by Dianna Geers
is licensed under CC0 1.0Some reuse the same password from an existing account
when creating a new account. - Some users, upon receiving an authentic-looking,
alarming (phishing) email about a problem with account access,
click on a conveniently provided link,
and submit their username and password
on an authentic-looking site -- directly to a hacker. - Enlightened attendees of my P@s$w0rdz or
Be Safer on the Internet courses hopefully use unique passwords,
don't click on email links, avoid fake sites,
monitor data breaches, and follow other privacy/security practices.

by GrahamKing is licensed under CC BY-NC-SA 2.0
Hackers
- Hackers don't usually try to log into accounts directly
by guessing passwords -- aka 'brute force', since it's too much work,
and most sites limit login attempts, though they might avoid such limits
by using botnets to attack from different IP addresses. - Hackers use phishing emails/sites to trick
careless users into providing credentials. - Hackers collect/share/sell lists of 'credentials'
-- usernames, passwords, credit cards and/or other info
-- from phishing attacks (careless users), and attacks/leaks/breaches
on various web sites/databases (sloppy company server security) -
"Hashing Password Bad" by Pluke, CC0, via Wikimedia Commons Usernames typically appear in plain text;
credential lists may or may not involve passwords:
most sites encode passwords as "hashes" (numerical codes);
amazingly, a few sites store passwords unencrypted as plain text! - Some of the known breaches in recent years:
Adobe, Anthem, Ashley Madison, Capital One, Charter,
Delta, Doordash, Elsevier, Equifax, Expedia/Orbitz,
Facebook, Hyatt, Kickstarter, Macys, Marriott/Starwood,
Panera, Sears, Slack, Sprint, T-Mobile, Under Armour,
Verizon, Whirlpool, Whole Foods, Zynga, ...
-- but notably not Zoom -
"Hashing Password Hashed" by Pluke, CC0, via Wikimedia Commons Credential stuffing: hackers run searches of known passwords (hashes) against the leaked credentials lists
- If one matches, hacker 'stuffs' those credentials into a different site.
- Hacker often succeeds in logging in
-- unless user had changed password or enabled other measures
Summary
- So, if a user had created a Zoom (or any new) account with a password phished from fake site
or reused from a different breached site, a hacker can easily login into Zoom
-- unless user had quickly changed password, or enabled MFA (paid account only?),
e.g.,Zoom > Admin > Advanced > Security > Sign in with Two-Factor Authentication -

Security by XKCD is licensed via
Creative Commons Attribution-NonCommercial 2.5Unfortunately, password reuse and clicking on phishing links are common
-- potential problems for any site, not just Zoom - So, who enabled the hackers?
The cause in this case (perhaps too bluntly),
PICNIC: "Problem In Chair, Not In Computer",
or PEBKAC: "Problem Exists Between Keyboard And Chair" - Strong password recommendations and other privacy/security advice are summarized above.
is licensed under CC BY-NC-SA 2.0
Two Types of Strong Passwords:
Memorable or Complex
- Memorable: for Devices & Password Manager (PM)
-- 2+ stored in your brain; entered manually (typable) - For phone, 8-10 digit passcode (default is often only 4-6 digits),
or alphanumeric. - For other tablets, computers & password managers,
memorable long (5+ word) phrase;
optional: numbers, capitals, punctuation, misspellings, etc. - Complex: for most Online Accounts
(and private key for FileVault or PM)
-- randomly generated by, stored in, filled-in by PM - If you don't have to remember or type it, why not make it as long and complex as site allows
(24-100 random characters) -- even for 'unimportant' sites? e.g.,
5iFt*b>Qyk[xpjrz@QoC2exanclhLvQ10izlX8hwxK6i=vwix14dwWVznQkvHrWh. - Autofill vs. Manual Entry: a PM may not be able to autofill passwords for certain sites/apps/services
- If you can manually copy/paste the password from PM
or duplicate it so that OS can autofill, e.g., Apple's Keychain,
a Complex password is great. - However, if a site disables paste, or a device has a primitive keyboard interface,
it's easier to enter a Memorable passphrase (minor punctuation, Shifting), e.g., Netflix login on a smart TV.
It may be possible to use another keyboard with the device, e.g., iOS Apple TV Remote app. - So, generally you'll need to remember just 2+ strong passwords,
and the password manager will store all others, which later it'll autofill or you'll paste or type.  In the next section, we'll look at how
In the next section, we'll look at how
to generate different kinds of passwords -- all unique, long and random:- Memorable and/or Typable by you: passcodes (PINs) and passphrases
-- for devices, password manager, sites - Complex [Pastable by PM] character sequences -- for everything else
- Refs: Password Strength; Credential Stuffing

is licensed under CC BY-NC-ND 2.0
How to Remember these Strong Passwords?
- "The only people who like change...
- For those who might forget or lose things -- or prefer to reduce brain clutter,
I strongly recommend using a "password manager" (PM) app. - We'll look at generating, testing and storing passwords;
setting device passwords; and using a PM in upcoming sections;
several PMs mentioned: 1Password, Bitwarden, Dashlane
-- with a focus on 1Password. - We'll discuss tradeoffs of other storage methods:
memory, paper, encrypted spreadsheet, your browser, etc. - 1PW video: No More Sticky Notes
- NYT article: Why You Need a Password Manager. Yes, You. (intro below)
A password manager is a secure, automated, all-digital replacement for the little notepad
that you might have all of your passwords scribbled down in now, but it’s also more than that.
Password managers generate strong new passwords when you create accounts or change a password,
and they store all of your passwords — and, in many cases, your credit card numbers, addresses,
bank accounts, and other information — in one place, protecting them with a single strong primary password.
If you remember your primary password, your password manager will remember everything else,
filling in your username and password for you whenever you log in to a site or app on your phone or computer.
It can proactively alert you when you’re reusing a password or when your passwords are
weak and easy to guess or hack, and some password managers will even let you know when
online accounts are hacked and your passwords have been exposed. For accounts that you need
to share with family members, friends, or co-workers — a joint bank account or mortgage site,
a shared Twitter account, or your insurance and medical records, for instance
— many password managers offer family plans that make it simple to share strong, complex
passwords without requiring multiple people to remember them or write them down.
Learning to use a password manager seems intimidating, but once you start using one
to make strong random passwords that you’re not on the hook to remember, you’ll wonder
how you lived without one. Usually, improving your digital security means making your devices
more annoying to use; a password manager is a rare opportunity to make yourself
more secure and less annoyed.
Before Jumping In...
- Maybe a password manager sounds great already and you're ready to jump in.
- If you're not tech savvy, wait until we introduce password managers in more detail in session 2.
- Otherwise, scan the rest of the course materials yourself,
paying special attention to a few items to avoid common problems. - Password Managers, esp. Getting Started
- Updating Passwords, esp. Strategy
- Recovery & User Names, esp. Recovery
- Wait to enable Multi-factor Authentication on your accounts -- to be covered in session 3.
