Introduction | Identity | How does MFA work? |
Setup: Email or SMS | Setup: TOTP (app)

is licensed under CC BY-NC 2.0
"Don't rely on passwords alone to protect anything you value.
Turn on multi-factor authentication (MFA) wherever possible"
Introduction
- Different usernames and random secret answers provide some protection.
- Use a more secure authentication factor in addition to a password,
especially for important accounts, e.g., financial, email
-- or for most accounts if you're a high-profile user. - Generally, a stronger second factor is a time-based (temporary) code
-- provided via SMS (texting), 'authenticator app' or physical token - Terminology for and implementation of this factor varies across sites
-- "Multi-Factor Authentication" (MFA) seems to be the latest preferred term,
but 2-Factor Authentication (2FA) and 2-Step Verification (2SV) commonly appear.
Other acronyms appearing below: SMS, TOTP, QR !! - Microsoft: 99.9% of compromised accounts did not use multi-factor authentication
Only 11% of all enterprise accounts use a MFA solution overall; ZD; 3/6/2020 - A Dutch security researcher says he logged into Trump's Twitter account
using the password “maga2020!” the account has now been secured w/ 2FA; 10/22/2020
-- with slightly different capitalization, this is also apparently the password for the Wi-Fi at Trump rallies. - Trump Twitter 'hack': Police accept attacker's claim BBC; 12/16/2020
is licensed under CC BY-NC-SA 2.0
Identity: Credentials & Authentication
- Credentials: "The combination of your username and password.
In some cases, additional pieces of information, such as your ZIP code
or the answers to security questions, may be considered part of your credentials
-- it's whatever a site or service needs to reliably identify you
as the authorized user of a given account." - Authentication: "The act of proving your identity to a computer system
-- typically by entering your credentials and having them confirmed as
matching the previously stored record." ~Take Control of Your Passwords - Authentication factors:
- knowledge ("something you know"): strong password remembered
or retrieved from a secure place; secret answers -

"Amazon AWS MFA Token Macro - 1"
by ChrisDag is licensed under CC BY 2.0possession ("something you have"): card, phone, physical token/device
- inherence ("something you are"): biometrics; fingerprint; facial recognition;
handwriting/typing/movement patterns; iris scan - The distinction between two-step verification (2SV)
and two-factor authentication (2FA) sounds straightforward: - 2SV: two credentials, e.g., password ('know') and secret answer ('know')
- 2FA: two different kinds (factors) of credentials, e.g., password ('know') and fingerprint ('are')
- However, there can be subtle differences, and sites may not use the technically correct label.
- We'll use MFA' generically here to refer to these; next: more detailed examples.
- single-factor authentication (SFA): e.g., password ('know') or biometrics (fingerprint, face; 'are')
- two-step verification (2SV), e.g., bank login: password ('know') and secret answer ('know')
-
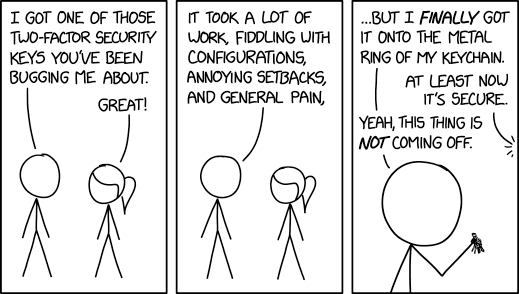
Two-Factor Security Key by XKCD is licensed
via Creative Commons Attribution-NonCommercial 2.5two-factor authentication (2FA), e.g.,
bank ATM: card ('have') + PIN ('know') or fingerprint ('are');
bank login: password ('know') + time-based code ('have')
-- some consider this 2SV ('know') if a hacker can intercept SMS message
or thief can access your device (texts, email, authentication app) - "While two-step verification (2SV) merely expands
single factor authentication (SFA) by requiring
two distinct verification occurrences of one authentication factor,
two-factor authentication (2FA) requires two occurrences,
each under a different category of credential."
~Two-factor authentication (2FA) versus two-step verification (2SV);
[authentication flowcharts]; Multi-factor authentication (MFA)
How Does Multi-Factor Authentication (MFA) Work? SMS, TOTP
- To increase security, you could receive a one-time time-based (expiring) code:
- 1. Sent from site via SMS (Short Message Service) text message to your phone
or email to your phone/computer. - 2. Sent from site via internet to a device/app, e.g., Facebook app, popup on 'trusted' Apple device
-

"Yubikey USB 2FA U2F Security Token"
by Tony Webster
is licensed under CC BY 2.03. TOTP (Time-based One Time Password) generated locally by authenticator app,
e.g., 1Password, Authy, Google Authenticator, Microsoft Authenticator - or by a physical security token, e.g., Yubikey
considerations: site support, browser support, hardware port connector; we won't be covering hardware keys - Locally generated TOTP codes are in sync with the codes expected by the requesting site.
- In addition to text/email, some sites can provide a code via voice call.
- If you don't see your preferred delivery method,
check if there's a link/button: "I need more options".  Enter (type or paste) this code into browser or device prompt
Enter (type or paste) this code into browser or device prompt- Security impact: someone with your password,
but without the time-based code,
would not be able to login from an unknown device. - Allow your browser, only on your private devices, to 'remember' via cookie:
your username and/or that you've been "trusted" (don't ask for MFA again) ? -
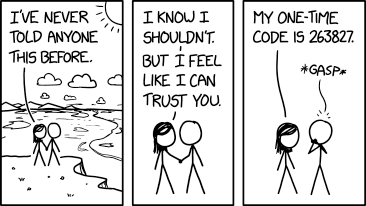
Never Told Anyone by XKCD is licensed
via Creative Commons Attribution-NonCommercial 2.5Although it seems like more work to provide userid, password and MFA code
each time you login, it's actually quite easy to autofill or paste from a password manager.
It's safer to always require MFA and never to reveal the code to others. - If you do forget to uncheck the box, you can later remove cookies to reset this 'permission'.
- Summary of possible common credential combinations -- from least to most secure:
- none: no or weak password
- SFA (single factor; know or are): PIN or fingerprint/face
- SFA (single factor; know or are): strong password
- 2SV (know/know): strong password + strong secret answer
- 2FA (know/have): strong password + code via SMS or email
- 2FA (know/have): strong password + TOTP code via authenticator app,
non-SMS app (Apple,Facebook) or hardware key - 2FA is not available for every site.
- It may be named or implemented in different ways.
- If you enable MFA/2FA, take note of how/where in case you want to disable it later.
 Sites that support 2FA: twofactorauth.org Categories:
Sites that support 2FA: twofactorauth.org Categories:
Backup & Sync; Banking; Betting; Cloud Computing; Communication;
Cryptocurrencies; Developer; Domains; Education; Email; Entertainment;
Finance; Food; Gaming; Government; Health; Hosting/VPS;
Identity Management; Investing; IoT; Legal; Payments; Remote Access;
Retail; Security; Social; Task Management; Transport; Utilities; VPN Providers;
e.g., Apple(iCloud), Dropbox, Google/Gmail, Facebook, Microsoft(Live),
Paypal, Twitter, Yahoo- Some sites provide backup codes,
-- useful if no phone or coverage, e.g., international travel;
or a recovery key in lieu of secret answers -- useful if phone stolen/lost;
e.g., AOL, Apple, Dropbox, Evernote, Facebook, Github, Gmail, Live - Store any recovery codes or backup key in PM
- Other fallback strategies: email, voice call, other SMS phone,
authenticator app -- or, disable MFA before a trip, re-enable afterwards. - It's useful to 'tag' login entries in PM, e.g., "MFA-SMS", "MFA-TOTP"
-- to find existing MFA accounts before getting rid of a phone,
setting up a new device, or considering a trip. - If you enable MFA for some sites where you use a separate app, especially email,
you may need an "app-specific password" (ASP) to allow the app to bypass MFA. - The site generates and manages ASPs
-- not your PM, though you could use PM to store ASP, and later copy into app manually.
Each site does things differently. In some cases, you may need a separate app, e.g., Comcast. - If the ASP is weaker than your regular password, or the setup process is complicated,
it might be better to have a strong regular password and not use MFA for that site. - Your "Application-Specific Passwords" Aren't Application-Specific How-to Geek; 11/2/2014
 Setting Up MFA via Email or SMS
Setting Up MFA via Email or SMS
- Email is a possible method to receive codes;
more available than SMS when travelling internationally?
no auto-extraction of code like SMS on Mac;
if device lacks strong password, SMS is better, TOTP (next section) best - SMS texting is the most common MFA method (and better than nothing),
but you may not have your phone, or there's no cell service,
or a phone number could be spoofed, or text messages intercepted;
in addition, providing a phone# can be a privacy leak on some sites,
e.g., Facebook, Twitter (which sell your info to marketers)  SMS on some sites may require U.S.-only phone #.
SMS on some sites may require U.S.-only phone #.- Apple-only? If using WiFi and cellular via WiFi,
iPhone might receive some SMS while travelling (even internationally) - If iPhone # is linked for AppleID, text messages can appear
in Messages app on other devices; - In many cases, macOS/iOS can extract MFA code
from text message; in iOS, code appears at top of keyboard;
in macOS, it's on clipboard to paste into Safari. - Link iPhone & iPad/Mac for Phone & Messages:
- Apple: Messages; Messages on Mac
- Apple: Make and receive calls on your Mac, iPad, or iPod touch
- Apple: Make and receive phone calls in FaceTime on Mac
- Cell carriers often set an account PIN to control changes to your account;
PIN may be set by default to last 4 digits of your SSN -- not exactly secret - A different PIN should prevent stealing of your phone # -- "SIM card hijacking";
contact customer support before a hacker does; record new PIN in Login entry for cell account. - Beware of phishing: some hackers provide email links to fake login pages,
which can capture not only your password, but also your time-based MFA code;
open & login to the correct page using your PM - If a text message with MFA code appears on your locked phone screen, consider disabling these notifications;
otherwise, someone with your stolen phone might be able to access your account
using the publicy visible MFA code, even without knowing your phone's passcode! - iOS:
Settings > Notifications > Messages > Show on Lock Screen: off - If supported, set up a 2nd phone number to receive code, e.g., spouse, in case you can't access primary phone,
e.g., Amazon, AOL, Apple, Chase, Evernote, Github, Gmail, Live, Paypal, Vanguard, Yahoo;
for some sites, if this 2nd phone is already associated with another account, it'll be unlinked, e.g., Facebook  Some sites send the code via a different secure communication protocol
Some sites send the code via a different secure communication protocol
(not SMS or email), though idiosyncratic.- Apple sends MFA code directly to 'trusted devices' (with same AppleID) via popup
- Some sites, e.g., Facebook, can send code to their own proprietary app.
 Setting Up MFA via TOTP in an Authenticator App
Setting Up MFA via TOTP in an Authenticator App
- Using TOTP (Time-based One Time Password)
is preferable to SMS text messaging and email
-- even though fewer sites support TOTP,
and it's a little more complex to set up & use.
Finding TOTP Sites
 Example sites: Amazon, Backblaze, Dreamhost, Dropbox, Evernote, Facebook,
Example sites: Amazon, Backblaze, Dreamhost, Dropbox, Evernote, Facebook,
Github, Google/Gmail, Instagram, LinkedIn, Microsoft(Live.com),
Paypal, Tumblr, Twitter, Uber, WordPress- for more, see: twofactorauth.org: "software token" label;
authy.com: "compatible with Authy" icon - 1Password also flags sites that support MFA;
some, e.g., eBay, may support only own app, and not general authenticator apps
-- add tag "2FA" to ignore/hide.
Authenticator Apps
- Example apps: 1Password, Authy, Bitwarden, Google Authenticator, Microsoft Authenticator
- Authy is a good choice for a separate app, with its multiple-device support and encryption.
- Some authenticator apps may require you to set up everything again if you upgrade to a new phone
-- Google Authenticator has recently added syncing capability;
if no encryption added, security of generated TOTP codes is only as strong as the device password. - Recent Apple devices can store/access 2FA settings in iCloud:
You Should Use Your iPhone's New Built-in Two-Factor Authentication
alternative to 3rd-party app; only iOS15, macOS 12? LH; 9/23/2021  1Password provides integrated support for "One-Time Passwords",
1Password provides integrated support for "One-Time Passwords",
so no separate authenticator app is needed.- 1Password:
(login item) > Edit > Label [...]:
One-time Password; scan QR/copy seed > Save - There are usually two methods for authenticator app & site to initialize and synchronize:

 1. Scan QR ("Quick Response") image provided by a site using a 'scanner window' [on right]
1. Scan QR ("Quick Response") image provided by a site using a 'scanner window' [on right]
or a device camera to initialize 'code generator'- 2. Copy an initial text 'seed code';
[far right]
paste into the authenticator app. - After Save, both app and remote server
will generate the same synchronized
sequence of random codes;
each code expires after a short interval.  To verify initially and to use after setup: enter or copy/paste code from authenticator app into site prompt;
To verify initially and to use after setup: enter or copy/paste code from authenticator app into site prompt;
countdown timer icon indicates how soon code will change (usually every ~0:30).- Upon logging into a site, 1PW copies TOTP code to clipboard,
allowing you to paste MFA code into browser (not apps?) w/o transcribing;
if you wait too long, display Login entry, Copy TOTP code, paste - If you later disable MFA for a site, remember to edit that Login entry:
remove One-Time Password field (for TOTP) and any MFA tag to avoid future confusion;
it's unclear if backup codes are invalid (and if they'd be requested);
if you re-enable MFA later, replace any old codes.
TOTP Setup Examples
- MFA setup process for each site is somewhat different, unfortunately.
- Start/practice with "less important" sites first, e.g., social media
- For email sites especially, be sure to have backup email & phone contacts in place.
- After you're comfortable, tackle more critical sites, e.g., finance,
and sites with more complex or multiple device dependencies, e.g., gmail, AppleID - These examples support TOTP (preferred); some may also support SMS:
- 1Password:
(Account) > More Actions... >
Manage Two-Factor Authentication Settings
1PW does not appear in 1PW's own list of sites that support MFA!
1PW TOTP setup needs to be stored in separate authenticator app, e.g., Authy -- not 1PW itself;
is this complexity worth the extra security? is site access already adequately protected by "secret key"? - Adobe:
Manage Your Account > Password and security >
Manage 2-Step Verification - Amazon:
Your Account > Login & Security >
Two-Step Verification (2SV) Settings - AppleID (Apple):
Security > Two-Factor Authentication - Backblaze:
Account > My Settings > Two-Factor Verification - BestBuy:
Account Settings > Account Security > Manage 2-Step Verification - Dropbox:
Account > Settings > Security > Two-step verification  Facebook:
Facebook: Settings > Security and Login >
Setup Extra Security > Use two-factor authentication:
Text Message, Code Generator (TOTP), Recovery Code- Google:
My Account > Sign-in & Security >
Signing into Google > 2-Step Verification - Instagram:
Settings > Privacy and Security >
Edit Two-Factor Authentication Setting - Intuit:
Account > Sign In & Security > Two-step verification - Linkedin:
Account > Login and security > 2-Step verification - Live (Microsoft):
Account > Security > more security options - Paypal:
Account > Security > 2-step verification - WordPress:
(Account) > Security > 2-Step Authentication - Zoom (Pro; paid account):
Admin > Advanced > Security > Sign in with Two-Factor Authentication - Refs: 2-Factor Authentication / 2-Step Verification
